121.[INSHack2017]rsa16m
查看题目
给了nec都很大
所以当m^e 严重小于n的时候。c很可能就是
m^e
所以对c开e次方就能得到m
import gmpy2
from Crypto.Util.number import *
#读取
data = open('rsa_16m.txt', 'r').read().split('\n')
#print(data)
m = gmpy2.iroot(int(data[1][4:], 16), int(data[2][4:], 16))[0]
#print(m)
#30156321943599743278455918182580886589695285093075236154009535613
print(long_to_bytes(m))#b'INSA{(I)NSA_W0uld_bE_pr0uD}'
122.[SUCTF2019]MT
from Crypto.Random import random
from Crypto.Util import number
from flag import flagdef convert(m):m = m ^ m >> 13m = m ^ m << 9 & 2029229568m = m ^ m << 17 & 2245263360m = m ^ m >> 19return mdef transform(message):assert len(message) % 4 == 0new_message = ''for i in range(len(message) / 4):block = message[i * 4 : i * 4 +4]block = number.bytes_to_long(block)block = convert(block)block = number.long_to_bytes(block, 4)new_message += blockreturn new_messagetransformed_flag = transform(flag[5:-1].decode('hex')).encode('hex')
print 'transformed_flag:', transformed_flag
# transformed_flag: 641460a9e3953b1aaa21f3a2
脚本
#python2
from Crypto.Random import random
from Crypto.Util import numberdef convert(m):m = m ^ m >> 13m = m ^ m << 9 & 2029229568m = m ^ m << 17 & 2245263360m = m ^ m >> 19return mdef transform(message):assert len(message) % 4 == 0new_message = ''for i in range(len(message) / 4):block = message[i * 4 : i * 4 +4]block = number.bytes_to_long(block)block = convert(block)block = number.long_to_bytes(block, 4)new_message += blockreturn new_message
def circle(m):t=mwhile True:x=tt=transform(t)if t==m:return x
transformed_flag='641460a9e3953b1aaa21f3a2'
flag = circle(transformed_flag.decode('hex')).encode('hex')
print('transformed_flag:', flag)
#84b45f89af22ce7e67275bdc
123-[De1CTF2019]xorz
查看题目
from itertools import *
from data import flag,plainkey=flag.strip("de1ctf{").strip("}")
assert(len(key)<38)
salt="WeAreDe1taTeam"
ki=cycle(key)
si=cycle(salt)
cipher = ''.join([hex(ord(p) ^ ord(next(ki)) ^ ord(next(si)))[2:].zfill(2) for p in plain])
print cipher
# output:
# 49380d773440222d1b421b3060380c3f403c3844791b202651306721135b6229294a3c3222357e766b2f15561b35305e3c3b670e49382c295c6c170553577d3a2b791470406318315d753f03637f2b614a4f2e1c4f21027e227a4122757b446037786a7b0e37635024246d60136f7802543e4d36265c3e035a725c6322700d626b345d1d6464283a016f35714d434124281b607d315f66212d671428026a4f4f79657e34153f3467097e4e135f187a21767f02125b375563517a3742597b6c394e78742c4a725069606576777c314429264f6e330d7530453f22537f5e3034560d22146831456b1b72725f30676d0d5c71617d48753e26667e2f7a334c731c22630a242c7140457a42324629064441036c7e646208630e745531436b7c51743a36674c4f352a5575407b767a5c747176016c0676386e403a2b42356a727a04662b4446375f36265f3f124b724c6e346544706277641025063420016629225b43432428036f29341a2338627c47650b264c477c653a67043e6766152a485c7f33617264780656537e5468143f305f4537722352303c3d4379043d69797e6f3922527b24536e310d653d4c33696c635474637d0326516f745e610d773340306621105a7361654e3e392970687c2e335f3015677d4b3a724a4659767c2f5b7c16055a126820306c14315d6b59224a27311f747f336f4d5974321a22507b22705a226c6d446a37375761423a2b5c29247163046d7e47032244377508300751727126326f117f7a38670c2b23203d4f27046a5c5e1532601126292f577776606f0c6d0126474b2a73737a41316362146e581d7c1228717664091c
脚本如下
import string
from binascii import unhexlify, hexlify
from itertools import *def bxor(a, b): # xor two byte strings of different lengthsif len(a) > len(b):return bytes([x ^ y for x, y in zip(a[:len(b)], b)])else:return bytes([x ^ y for x, y in zip(a, b[:len(a)])])def hamming_distance(b1, b2):differing_bits = 0for byte in bxor(b1, b2):differing_bits += bin(byte).count("1")return differing_bitsdef break_single_key_xor(text):key = 0possible_space = 0max_possible = 0letters = string.ascii_letters.encode('ascii')for a in range(0, len(text)):maxpossible = 0for b in range(0, len(text)):if(a == b):continuec = text[a] ^ text[b]if c not in letters and c != 0:continuemaxpossible += 1if maxpossible > max_possible:max_possible = maxpossiblepossible_space = akey = text[possible_space] ^ 0x20return chr(key)salt = "WeAreDe1taTeam"
si = cycle(salt)
b = unhexlify(b'49380d773440222d1b421b3060380c3f403c3844791b202651306721135b6229294a3c3222357e766b2f15561b35305e3c3b670e49382c295c6c170553577d3a2b791470406318315d753f03637f2b614a4f2e1c4f21027e227a4122757b446037786a7b0e37635024246d60136f7802543e4d36265c3e035a725c6322700d626b345d1d6464283a016f35714d434124281b607d315f66212d671428026a4f4f79657e34153f3467097e4e135f187a21767f02125b375563517a3742597b6c394e78742c4a725069606576777c314429264f6e330d7530453f22537f5e3034560d22146831456b1b72725f30676d0d5c71617d48753e26667e2f7a334c731c22630a242c7140457a42324629064441036c7e646208630e745531436b7c51743a36674c4f352a5575407b767a5c747176016c0676386e403a2b42356a727a04662b4446375f36265f3f124b724c6e346544706277641025063420016629225b43432428036f29341a2338627c47650b264c477c653a67043e6766152a485c7f33617264780656537e5468143f305f4537722352303c3d4379043d69797e6f3922527b24536e310d653d4c33696c635474637d0326516f745e610d773340306621105a7361654e3e392970687c2e335f3015677d4b3a724a4659767c2f5b7c16055a126820306c14315d6b59224a27311f747f336f4d5974321a22507b22705a226c6d446a37375761423a2b5c29247163046d7e47032244377508300751727126326f117f7a38670c2b23203d4f27046a5c5e1532601126292f577776606f0c6d0126474b2a73737a41316362146e581d7c1228717664091c')
plain = ''.join([hex(ord(c) ^ ord(next(si)))[2:].zfill(2) for c in b.decode()])
b = unhexlify(plain)
print(plain)normalized_distances = []for KEYSIZE in range(2, 40):# 我们取其中前6段计算平局汉明距离b1 = b[: KEYSIZE]b2 = b[KEYSIZE: KEYSIZE * 2]b3 = b[KEYSIZE * 2: KEYSIZE * 3]b4 = b[KEYSIZE * 3: KEYSIZE * 4]b5 = b[KEYSIZE * 4: KEYSIZE * 5]b6 = b[KEYSIZE * 5: KEYSIZE * 6]normalized_distance = float(hamming_distance(b1, b2) +hamming_distance(b2, b3) +hamming_distance(b3, b4) +hamming_distance(b4, b5) +hamming_distance(b5, b6)) / (KEYSIZE * 5)normalized_distances.append((KEYSIZE, normalized_distance))
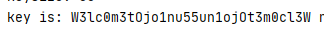
normalized_distances = sorted(normalized_distances, key=lambda x: x[1])for KEYSIZE, _ in normalized_distances[:5]:block_bytes = [[] for _ in range(KEYSIZE)]for i, byte in enumerate(b):block_bytes[i % KEYSIZE].append(byte)keys = ''try:for bbytes in block_bytes:keys += break_single_key_xor(bbytes)key = bytearray(keys * len(b), "utf-8")plaintext = bxor(b, key)print("keysize:", KEYSIZE)print("key is:", keys, "n")s = bytes.decode(plaintext)print(s)except Exception:continue运行得到
124.[INSHack2019]Yet Another RSA Challenge - Part 1
查看题目719579745653303119025873098043848913976880838286635817351790189702008424828505522253331968992725441130409959387942238566082746772468987336980704680915524591881919460709921709513741059003955050088052599067720107149755856317364317707629467090624585752920523062378696431510814381603360130752588995217840721808871896469275562085215852034302374902524921137398710508865248881286824902780186249148613287250056380811479959269915786545911048030947364841177976623684660771594747297272818410589981294227084173316280447729440036251406684111603371364957690353449585185893322538541593242187738587675489180722498945337715511212885934126635221601469699184812336984707723198731876940991485904637481371763302337637617744175461566445514603405016576604569057507997291470369704260553992902776099599438704680775883984720946337235834374667842758010444010254965664863296455406931885650448386682827401907759661117637294838753325610213809162253020362015045242003388829769019579522792182295457962911430276020610658073659629786668639126004851910536565721128484604554703970965744790413684836096724064390486888113608024265771815004188203124405817878645103282802994701531113849607969243815078720289912255827700390198089699808626116357304202660642601149742427766381 0xDCC5A0BD3A1FC0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331AFCFD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14FCD2739D76E69283E57DDB11FC531B4611EE3 596380963583874022971492302071822444225514552231574984926542429117396590795270181084030717066220888052607057994262255729890598322976783889090993129161030148064314476199052180347747135088933481343974996843632511300255010825580875930722684714290535684951679115573751200980708359500292172387447570080875531002842462002727646367063816531958020271149645805755077133231395881833164790825731218786554806777097126212126561056170733032553159740167058242065879953688453169613384659653035659118823444582576657499974059388261153064772228570460351169216103620379299362366574826080703907036316546232196313193923841110510170689800892941998845140534954264505413254429240789223724066502818922164419890197058252325607667959185100118251170368909192832882776642565026481260424714348087206462283972676596101498123547647078981435969530082351104111747783346230914935599764345176602456069568419879060577771404946743580809330315332836749661503035076868102720709045692483171306425207758972682717326821412843569770615848397477633761506670219845039890098105484693890695897858251238713238301401843678654564558196040100908796513657968507381392735855990706254646471937809011610992016368630851454275478216664521360246605400986428230407975530880206404171034278692756
import subprocess
p = subprocess.check_output('openssl prime -generate -bits 2048 -hex')
q = subprocess.check_output('openssl prime -generate -bits 2048 -hex')
flag = int('INSA{REDACTED}'.encode('hex'), 16)N = int(p,16) * int(q,16)
print N
print '0x'+p.replace('9F','FC')
print pow(flag,65537,N)
这道题告诉你了rsa的n的因子其中的p,但是其中的字母有所替换,我们就可以发现,这串字符中的‘FC’可能是’FC‘也可能是’9F’于是话不多说直接爆破即可,下面给出本题脚本
import gmpy2
from Crypto.Util.number import *
n=719579745653303119025873098043848913976880838286635817351790189702008424828505522253331968992725441130409959387942238566082746772468987336980704680915524591881919460709921709513741059003955050088052599067720107149755856317364317707629467090624585752920523062378696431510814381603360130752588995217840721808871896469275562085215852034302374902524921137398710508865248881286824902780186249148613287250056380811479959269915786545911048030947364841177976623684660771594747297272818410589981294227084173316280447729440036251406684111603371364957690353449585185893322538541593242187738587675489180722498945337715511212885934126635221601469699184812336984707723198731876940991485904637481371763302337637617744175461566445514603405016576604569057507997291470369704260553992902776099599438704680775883984720946337235834374667842758010444010254965664863296455406931885650448386682827401907759661117637294838753325610213809162253020362015045242003388829769019579522792182295457962911430276020610658073659629786668639126004851910536565721128484604554703970965744790413684836096724064390486888113608024265771815004188203124405817878645103282802994701531113849607969243815078720289912255827700390198089699808626116357304202660642601149742427766381
#p="DCC5A0BD3A1"+a+"0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331A"+b+"FD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14"+c+"D2739D76E69283E57DDB11"+d+"531B4611EE3"
cipher=596380963583874022971492302071822444225514552231574984926542429117396590795270181084030717066220888052607057994262255729890598322976783889090993129161030148064314476199052180347747135088933481343974996843632511300255010825580875930722684714290535684951679115573751200980708359500292172387447570080875531002842462002727646367063816531958020271149645805755077133231395881833164790825731218786554806777097126212126561056170733032553159740167058242065879953688453169613384659653035659118823444582576657499974059388261153064772228570460351169216103620379299362366574826080703907036316546232196313193923841110510170689800892941998845140534954264505413254429240789223724066502818922164419890197058252325607667959185100118251170368909192832882776642565026481260424714348087206462283972676596101498123547647078981435969530082351104111747783346230914935599764345176602456069568419879060577771404946743580809330315332836749661503035076868102720709045692483171306425207758972682717326821412843569770615848397477633761506670219845039890098105484693890695897858251238713238301401843678654564558196040100908796513657968507381392735855990706254646471937809011610992016368630851454275478216664521360246605400986428230407975530880206404171034278692756
plain=['9F','FC']
for a in plain:for b in plain:for c in plain:for d in plain:p="DCC5A0BD3A1"+a+"0BEB0DA1C2E8CF6B474481B7C12849B76E03C4C946724DB577D2825D6AA193DB559BC9DBABE1DDE8B5E7805E48749EF002F622F7CDBD7853B200E2A027E87E331A"+b+"FD066ED9900F1E5F5E5196A451A6F9E329EB889D773F08E5FBF45AACB818FD186DD74626180294DCC31805A88D1B71DE5BFEF3ED01F12678D906A833A78EDCE9BDAF22BBE45C0BFB7A82AFE42C1C3B8581C83BF43DFE31BFD81527E507686956458905CC9A660604552A060109DC81D01F229A264AB67C6D7168721AB36DE769CEAFB97F238050193EC942078DDF5329A387F46253A4411A9C8BB71F9AEB11AC9623E41C14"+c+"D2739D76E69283E57DDB11"+d+"531B4611EE3"p1=int(p,16)if(n%p1==0):print p1#27869881035956015184979178092922248885674897320108269064145135676677416930908750101386898785101159450077433625380803555071301130739332256486285289470097290409044426739584302074834857801721989648648799253740641480496433764509396039330395579654527851232078667173592401475356727873045602595552393666889257027478385213547302885118341490346766830846876201911076530008127691612594913799272782226366932754058372641521481522494577124999360890113778202218378165756595787931498460866236502220175258385407478826827807650036729385244897815805427164434537088709092238894902485613707990645011133078730017425033369999448757627854563
e=65537
p=27869881035956015184979178092922248885674897320108269064145135676677416930908750101386898785101159450077433625380803555071301130739332256486285289470097290409044426739584302074834857801721989648648799253740641480496433764509396039330395579654527851232078667173592401475356727873045602595552393666889257027478385213547302885118341490346766830846876201911076530008127691612594913799272782226366932754058372641521481522494577124999360890113778202218378165756595787931498460866236502220175258385407478826827807650036729385244897815805427164434537088709092238894902485613707990645011133078730017425033369999448757627854563
q=n//p
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
m=pow(cipher,d,n)
print long_to_bytes(m)
#INSA{I_w1ll_us3_OTp_n3xT_T1M3}125.[GUET-CTF2019]NO SOS
查看题目..-.-.-.–…….–..-…-..-…–.-.-….-..-..–.-.-..-.-..—-
像不像摩斯密码,NO SOS说明不是摩斯密码,.-转成二进制
用培根密码解密即可
flag{guetkkp}
126.[UTCTF2020]OTP
传说中的读题就行
127.[QCTF2018]Xman-RSA
查看题目
首先看到encryption.encrypted这个文件感觉就很像是被加密的加密脚本
词频分析后得到大致的结果,但是发现还有一些错误,然后手动修改还原得到原加密脚本。
得到原脚本
from gmpy2 import is_prime
from os import urandom
import base64def bytes_to_num(b):return int(b.encode('hex'), 16)
def num_to_bytes(n):b = hex(n)[2:-1]b = '0' + b if len(b) % 2 == 1 else breturn b.decode('hex')
def get_a_prime(l):random_Teed = urandom(l)num = bytes_to_num(random_Teed)while True:if is_prime(num):breaknum+= 1return numdef encrypt(s, e, n):p = bytes_to_num(s)p = pow(p, e, n)return num_to_bytes(p).encode('hex')
def separate(n):p = n % 4t = (p * p) % 4return t == 1
f = open('flag.txt', 'r')
flag = f.read()
msg1 = ""
msg2 = ""
for i in range(len(flag)):if separate(i):msg2 += flag[i]else:msg1 += flag[i]
p1 = get_a_prime(128)
p2 = get_a_prime(128)
p3 = get_a_prime(128)
n1 = p1 * p2
n2 = p1 * p3
e = 0x1001
c1 = encrypt(msg1, e, n1)
c2 = encrypt(msg2, e, n2)
print(c1)
print(c2)
e1 = 0x1001
e2 = 0x101
p4 = get_a_prime(128)
p5 = get_a_prime(128)
n3 = p4 * p5
c1 = num_to_bytes(pow(n1, e1, n3)).encode('hex')
c2 = num_to_bytes(pow(n1, e2, n3)).encode('hex')
print(c1)
print(c2)
print(base64.b64encode(num_to_bytes(n2)))
print(base64.b64encode(num_to_bytes(n3)))再从另外三个文件里面找出给的条件
e1 = 0x1001
e2 = 0x101
e = 0x1001
n2='PVNHb2BfGAnmxLrbKhgsYXRwWIL9eOj6K0s3I0slKHCTXTAUtZh3T0r+RoSlhpO3+77AY8P7WETYz2Jzuv5FV/mMODoFrM5fMyQsNt90VynR6J3Jv+fnPJPsm2hJ1Fqt7EKaVRwCbt6a4BdcRoHJsYN/+eh7k/X+FL5XM7viyvQxyFawQrhSV79FIoX6xfjtGW+uAeVF7DScRcl49dlwODhFD7SeLqzoYDJPIQS+VSb3YtvrDgdV+EhuS1bfWvkkXRijlJEpLrgWYmMdfsYX8u/+Ylf5xcBGn3hv1YhQrBCg77AHuUF2w/gJ/ADHFiMcH3ux3nqOsuwnbGSr7jA6Cw=='
n3='TmNVbWUhCXR1od3gBpM+HGMKK/4ErfIKITxomQ/QmNCZlzmmsNyPXQBiMEeUB8udO7lWjQTYGjD6k21xjThHTNDG4z6C2cNNPz73VIaNTGz0hrh6CmqDowFbyrk+rv53QSkVKPa8EZnFKwGz9B3zXimm1D+01cov7V/ZDfrHrEjsDkgK4ZlrQxPpZAPl+yqGlRK8soBKhY/PF3/GjbquRYeYKbagpUmWOhLnF4/+DP33ve/EpaSAPirZXzf8hyatL4/5tAZ0uNq9W6T4GoMG+N7aS2GeyUA2sLJMHymW4cFK5l5kUvjslRdXOHTmz5eHxqIV6TmSBQRgovUijlNamQ=='
c11=0x2639c28e3609a4a8c953cca9c326e8e062756305ae8aee6efcd346458aade3ee8c2106ab9dfe5f470804f366af738aa493fd2dc26cb249a922e121287f3eddec0ed8dea89747dc57aed7cd2089d75c23a69bf601f490a64f73f6a583081ae3a7ed52238c13a95d3322065adba9053ee5b12f1de1873dbad9fbf4a50a2f58088df0fddfe2ed8ca1118c81268c8c0fd5572494276f4e48b5eb424f116e6f5e9d66da1b6b3a8f102539b690c1636e82906a46f3c5434d5b04ed7938861f8d453908970eccef07bf13f723d6fdd26a61be8b9462d0ddfbedc91886df194ea022e56c1780aa6c76b9f1c7d5ea743dc75cec3c805324e90ea577fa396a1effdafa3090
c22=0x42ff1157363d9cd10da64eb4382b6457ebb740dbef40ade9b24a174d0145adaa0115d86aa2fc2a41257f2b62486eaebb655925dac78dd8d13ab405aef5b8b8f9830094c712193500db49fb801e1368c73f88f6d8533c99c8e7259f8b9d1c926c47215ed327114f235ba8c873af7a0052aa2d32c52880db55c5615e5a1793b690c37efdd5e503f717bb8de716303e4d6c4116f62d81be852c5d36ef282a958d8c82cf3b458dcc8191dcc7b490f227d1562b1d57fbcf7bf4b78a5d90cd385fd79c8ca4688e7d62b3204aeaf9692ba4d4e44875eaa63642775846434f9ce51d138ca702d907849823b1e86896e4ea6223f93fae68b026cfe5fa5a665569a9e3948a
c1=0x1240198b148089290e375b999569f0d53c32d356b2e95f5acee070f016b3bef243d0b5e46d9ad7aa7dfe2f21bda920d0ac7ce7b1e48f22b2de410c6f391ce7c4347c65ffc9704ecb3068005e9f35cbbb7b27e0f7a18f4f42ae572d77aaa3ee189418d6a07bab7d93beaa365c98349d8599eb68d21313795f380f05f5b3dfdc6272635ede1f83d308c0fdb2baf444b9ee138132d0d532c3c7e60efb25b9bf9cb62dba9833aa3706344229bd6045f0877661a073b6deef2763452d0ad7ab3404ba494b93fd6dfdf4c28e4fe83a72884a99ddf15ca030ace978f2da87b79b4f504f1d15b5b96c654f6cd5179b72ed5f84d3a16a8f0d5bf6774e7fd98d27bf3c9839
c2=0x129d5d4ab3f9e8017d4e6761702467bbeb1b884b6c4f8ff397d078a8c41186a3d52977fa2307d5b6a0ad01fedfc3ba7b70f776ba3790a43444fb954e5afd64b1a3abeb6507cf70a5eb44678a886adf81cb4848a35afb4db7cd7818f566c7e6e2911f5ababdbdd2d4ff9825827e58d48d5466e021a64599b3e867840c07e29582961f81643df07f678a61a9f9027ebd34094e272dfbdc4619fa0ac60f0189af785df77e7ec784e086cf692a7bf7113a7fb8446a65efa8b431c6f72c14bcfa49c9b491fb1d87f2570059e0f13166a85bb555b40549f45f04bc5dbd09d8b858a5382be6497d88197ffb86381085756365bd757ec3cdfa8a77ba1728ec2de596c5ab通过分析代码,第一步先通过共模攻击得到n1,然后通过最大公因数得到p1,顺势分解n1,n2,然后逆过去就可以得到flag
解密脚本
import base64
import Crypto.Util.number
import gmpy2e1 = 0x1001
e2 = 0x101
e = 0x1001
n2='PVNHb2BfGAnmxLrbKhgsYXRwWIL9eOj6K0s3I0slKHCTXTAUtZh3T0r+RoSlhpO3+77AY8P7WETYz2Jzuv5FV/mMODoFrM5fMyQsNt90VynR6J3Jv+fnPJPsm2hJ1Fqt7EKaVRwCbt6a4BdcRoHJsYN/+eh7k/X+FL5XM7viyvQxyFawQrhSV79FIoX6xfjtGW+uAeVF7DScRcl49dlwODhFD7SeLqzoYDJPIQS+VSb3YtvrDgdV+EhuS1bfWvkkXRijlJEpLrgWYmMdfsYX8u/+Ylf5xcBGn3hv1YhQrBCg77AHuUF2w/gJ/ADHFiMcH3ux3nqOsuwnbGSr7jA6Cw=='
n3='TmNVbWUhCXR1od3gBpM+HGMKK/4ErfIKITxomQ/QmNCZlzmmsNyPXQBiMEeUB8udO7lWjQTYGjD6k21xjThHTNDG4z6C2cNNPz73VIaNTGz0hrh6CmqDowFbyrk+rv53QSkVKPa8EZnFKwGz9B3zXimm1D+01cov7V/ZDfrHrEjsDkgK4ZlrQxPpZAPl+yqGlRK8soBKhY/PF3/GjbquRYeYKbagpUmWOhLnF4/+DP33ve/EpaSAPirZXzf8hyatL4/5tAZ0uNq9W6T4GoMG+N7aS2GeyUA2sLJMHymW4cFK5l5kUvjslRdXOHTmz5eHxqIV6TmSBQRgovUijlNamQ=='
c11=0x2639c28e3609a4a8c953cca9c326e8e062756305ae8aee6efcd346458aade3ee8c2106ab9dfe5f470804f366af738aa493fd2dc26cb249a922e121287f3eddec0ed8dea89747dc57aed7cd2089d75c23a69bf601f490a64f73f6a583081ae3a7ed52238c13a95d3322065adba9053ee5b12f1de1873dbad9fbf4a50a2f58088df0fddfe2ed8ca1118c81268c8c0fd5572494276f4e48b5eb424f116e6f5e9d66da1b6b3a8f102539b690c1636e82906a46f3c5434d5b04ed7938861f8d453908970eccef07bf13f723d6fdd26a61be8b9462d0ddfbedc91886df194ea022e56c1780aa6c76b9f1c7d5ea743dc75cec3c805324e90ea577fa396a1effdafa3090
c22=0x42ff1157363d9cd10da64eb4382b6457ebb740dbef40ade9b24a174d0145adaa0115d86aa2fc2a41257f2b62486eaebb655925dac78dd8d13ab405aef5b8b8f9830094c712193500db49fb801e1368c73f88f6d8533c99c8e7259f8b9d1c926c47215ed327114f235ba8c873af7a0052aa2d32c52880db55c5615e5a1793b690c37efdd5e503f717bb8de716303e4d6c4116f62d81be852c5d36ef282a958d8c82cf3b458dcc8191dcc7b490f227d1562b1d57fbcf7bf4b78a5d90cd385fd79c8ca4688e7d62b3204aeaf9692ba4d4e44875eaa63642775846434f9ce51d138ca702d907849823b1e86896e4ea6223f93fae68b026cfe5fa5a665569a9e3948a
c1=0x1240198b148089290e375b999569f0d53c32d356b2e95f5acee070f016b3bef243d0b5e46d9ad7aa7dfe2f21bda920d0ac7ce7b1e48f22b2de410c6f391ce7c4347c65ffc9704ecb3068005e9f35cbbb7b27e0f7a18f4f42ae572d77aaa3ee189418d6a07bab7d93beaa365c98349d8599eb68d21313795f380f05f5b3dfdc6272635ede1f83d308c0fdb2baf444b9ee138132d0d532c3c7e60efb25b9bf9cb62dba9833aa3706344229bd6045f0877661a073b6deef2763452d0ad7ab3404ba494b93fd6dfdf4c28e4fe83a72884a99ddf15ca030ace978f2da87b79b4f504f1d15b5b96c654f6cd5179b72ed5f84d3a16a8f0d5bf6774e7fd98d27bf3c9839
c2=0x129d5d4ab3f9e8017d4e6761702467bbeb1b884b6c4f8ff397d078a8c41186a3d52977fa2307d5b6a0ad01fedfc3ba7b70f776ba3790a43444fb954e5afd64b1a3abeb6507cf70a5eb44678a886adf81cb4848a35afb4db7cd7818f566c7e6e2911f5ababdbdd2d4ff9825827e58d48d5466e021a64599b3e867840c07e29582961f81643df07f678a61a9f9027ebd34094e272dfbdc4619fa0ac60f0189af785df77e7ec784e086cf692a7bf7113a7fb8446a65efa8b431c6f72c14bcfa49c9b491fb1d87f2570059e0f13166a85bb555b40549f45f04bc5dbd09d8b858a5382be6497d88197ffb86381085756365bd757ec3cdfa8a77ba1728ec2de596c5abn2=Crypto.Util.number.bytes_to_long(base64.b64decode(n2))
n3=Crypto.Util.number.bytes_to_long(base64.b64decode(n3))def exgcd(m, n, x, y):if n == 0:x = 1y = 0return (m, x, y)a1 = b = 1a = b1 = 0c = md = nq = int(c / d)r = c % dwhile r:c = dd = rt = a1a1 = aa = t - q * at = b1b1 = bb = t - q * bq = int(c / d)r = c % dx = ay = breturn (d, x, y)#扩展欧几里得算法
def separate(n):p = n % 4t = (p * p) % 4return t == 1
ans=exgcd(e1,e2,0,0)
s1=ans[1]
s2=ans[2]
n1=(gmpy2.powmod(c11,s1,n3)*gmpy2.powmod(c22,s2,n3))%n3#powmod()函数真香,分数取模也可直接算,一开始不知道还去找了很多的算法知识
p1=gmpy2.gcd(n1,n2)
p2=n1//p1
p3=n2//p1
phi1=(p1-1)*(p2-1)
phi2=(p1-1)*(p3-1)
d1=gmpy2.invert(e,phi1)
d2=gmpy2.invert(e,phi2)
m1=gmpy2.powmod(c1,d1,n1)
m2=gmpy2.powmod(c2,d2,n2)
m1=Crypto.Util.number.long_to_bytes(m1).decode()
m2=Crypto.Util.number.long_to_bytes(m2).decode()
length=len(m1)+len(m2)
flag=''
temp1=0
temp2=0
for i in range(length):if separate(i):flag+=m2[temp2]temp2=temp2+1else:flag+=m1[temp1]temp1=temp1+1
print(flag)
运行得到flag
XMAN{CRYPT0_I5_50_Interestingvim rsa.py}
128.[ACTF新生赛2020]crypto-des
两个文件一个压缩包
import struct
import binasciis=[72065910510177138000000000000000.000000,71863209670811371000000.000000,18489682625412760000000000000000.000000,72723257588050687000000.000000,4674659167469766200000000.000000,19061698837499292000000000000000000000.000000]
a=''
b=''
for i in s:i=float(i)tmp=struct.pack('<f', i).hex()#小端a+=tmpfor j in s:j=float(j)tmp=struct.pack('>f', j).hex()#大端b+=tmpprint (binascii.a2b_hex(a))
print (binascii.a2b_hex(b))
运行得到压缩包密码
import pyDes
import base64
from FLAG import flag
deskey = "********"
DES = pyDes.des(deskey)
DES.setMode('ECB')
DES.Kn = [[1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 1, 0, 1, 1, 0, 0, 1, 0, 0, 0, 1, 1, 0, 0, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 1, 1, 0, 0, 0],[1, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 1, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0, 0, 1, 0, 1, 1, 0, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 1, 0, 0, 1, 1, 0], [0, 1, 1, 0, 0, 1, 0, 0, 1, 1, 0, 1, 0, 1, 1, 0, 0, 1, 1, 1, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 0, 0, 1, 0, 0],[1, 1, 0, 0, 0, 1, 1, 0, 1, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 1, 1, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1], [0, 0, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 1, 0, 1, 0, 1, 0, 0, 1, 1, 0, 1, 1, 0, 0, 1, 1, 1, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1],[0, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 1, 0, 1, 1, 1, 0, 1, 0, 1, 0, 1, 1, 0, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 0],[0, 0, 1, 0, 1, 0, 1, 1, 0, 0, 0, 0, 0, 0, 0, 1, 1, 1, 0, 1, 1, 0, 0, 1, 0, 0, 1, 0, 1, 1, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1, 0, 0, 0, 0, 0, 1, 1, 0],[0, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 0, 0, 0, 1, 0, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 1, 1, 1, 0, 0, 1, 1, 0],[1, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 1, 0, 0, 1, 0, 0, 0, 0, 1, 0, 0, 0, 0, 0, 0, 1, 1, 1, 1, 1, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0],[0, 0, 0, 1, 0, 0, 1, 0, 0, 1, 1, 0, 1, 0, 0, 1, 1, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 0, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 0, 1, 1, 1, 0, 0, 0],[0, 0, 0, 1, 1, 0, 0, 1, 0, 0, 1, 0, 1, 1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 1, 1, 1, 0, 0, 0, 0, 0, 0, 1, 0, 1, 1],[0, 1, 0, 0, 0, 0, 0, 1, 0, 0, 1, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 1, 0, 1, 0, 0, 0, 0, 1, 1, 1, 0, 0, 1, 0, 1, 0, 0, 1, 0, 0, 0, 1, 1, 1, 1, 1, 0],[1, 1, 0, 1, 0, 0, 0, 1, 1, 0, 1, 0, 0, 1, 0, 0, 1, 0, 1, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 1, 0, 0, 1, 1, 1, 1, 0, 0, 1, 0, 0],[1, 1, 0, 1, 0, 0, 0, 0, 1, 0, 0, 0, 1, 1, 1, 0, 1, 0, 1, 0, 0, 0, 1, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 1, 1, 1, 1, 0, 0, 0, 1],[1, 1, 1, 1, 0, 0, 0, 0, 1, 0, 1, 1, 0, 0, 1, 0, 0, 0, 1, 0, 0, 1, 1, 0, 1, 1, 0, 0, 0, 0, 1, 1, 1, 0, 1, 0, 1, 1, 1, 0, 0, 0, 0, 1, 0, 1, 0, 1],[1, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 1, 1, 1, 1, 0, 0, 0, 1, 0, 0, 1, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0, 0, 1, 0, 0, 0, 0, 0, 1, 0, 1, 1]]
cipher_list = base64.b64encode(DES.encrypt(flag))
#b'vrkgBqeK7+h7mPyWujP8r5FqH5yyVlqv0CXudqoNHVAVdNO8ML4lM4zgez7weQXo'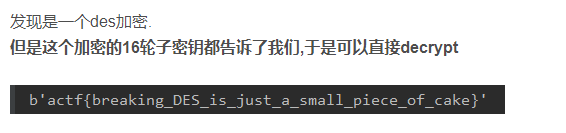
129.[watevrCTF 2019]Swedish RSA
查看题目
flag = bytearray(raw_input())
flag = list(flag)
length = len(flag)
bits = 16## Prime for Finite Field.
p = random_prime(2^bits-1, False, 2^(bits-1))file_out = open("downloads/polynomial_rsa.txt", "w")
file_out.write("Prime: " + str(p) + "\n")## Univariate Polynomial Ring in y over Finite Field of size p
R.<y> = PolynomialRing(GF(p))## Analogous to the primes in Z
def gen_irreducable_poly(deg):while True:out = R.random_element(degree=deg)if out.is_irreducible():return out#生成一个“素数”多项式## Polynomial "primes"
P = gen_irreducable_poly(ZZ.random_element(length, 2*length))
Q = gen_irreducable_poly(ZZ.random_element(length, 2*length))## Public exponent key
e = 65537## Modulus
N = P*Q
file_out.write("Modulus: " + str(N) + "\n")## Univariate Quotient Polynomial Ring in x over Finite Field of size 659 with modulus N(x)
S.<x> = R.quotient(N)## Encrypt
m = S(flag)
c = m^efile_out.write("Ciphertext: " + str(c))
file_out.close()Prime: 43753
Modulus: 34036*y^177 + 23068*y^176 + 13147*y^175 + 36344*y^174 + 10045*y^173 + 41049*y^172 + 17786*y^171 + 16601*y^170 + 7929*y^169 + 37570*y^168 + 990*y^167 + 9622*y^166 + 39273*y^165 + 35284*y^164 + 15632*y^163 + 18850*y^162 + 8800*y^161 + 33148*y^160 + 12147*y^159 + 40487*y^158 + 6407*y^157 + 34111*y^156 + 8446*y^155 + 21908*y^154 + 16812*y^153 + 40624*y^152 + 43506*y^151 + 39116*y^150 + 33011*y^149 + 23914*y^148 + 2210*y^147 + 23196*y^146 + 43359*y^145 + 34455*y^144 + 17684*y^143 + 25262*y^142 + 982*y^141 + 24015*y^140 + 27968*y^139 + 37463*y^138 + 10667*y^137 + 39519*y^136 + 31176*y^135 + 27520*y^134 + 32118*y^133 + 8333*y^132 + 38945*y^131 + 34713*y^130 + 1107*y^129 + 43604*y^128 + 4433*y^127 + 18110*y^126 + 17658*y^125 + 32354*y^124 + 3219*y^123 + 40238*y^122 + 10439*y^121 + 3669*y^120 + 8713*y^119 + 21027*y^118 + 29480*y^117 + 5477*y^116 + 24332*y^115 + 43480*y^114 + 33406*y^113 + 43121*y^112 + 1114*y^111 + 17198*y^110 + 22829*y^109 + 24424*y^108 + 16523*y^107 + 20424*y^106 + 36206*y^105 + 41849*y^104 + 3584*y^103 + 26500*y^102 + 31897*y^101 + 34640*y^100 + 27449*y^99 + 30962*y^98 + 41434*y^97 + 22125*y^96 + 24314*y^95 + 3944*y^94 + 18400*y^93 + 38476*y^92 + 28904*y^91 + 27936*y^90 + 41867*y^89 + 25573*y^88 + 25659*y^87 + 33443*y^86 + 18435*y^85 + 5934*y^84 + 38030*y^83 + 17563*y^82 + 24086*y^81 + 36782*y^80 + 20922*y^79 + 38933*y^78 + 23448*y^77 + 10599*y^76 + 7156*y^75 + 29044*y^74 + 23605*y^73 + 7657*y^72 + 28200*y^71 + 2431*y^70 + 3860*y^69 + 23259*y^68 + 14590*y^67 + 33631*y^66 + 15673*y^65 + 36049*y^64 + 29728*y^63 + 22413*y^62 + 18602*y^61 + 18557*y^60 + 23505*y^59 + 17642*y^58 + 12595*y^57 + 17255*y^56 + 15316*y^55 + 8948*y^54 + 38*y^53 + 40329*y^52 + 9823*y^51 + 5798*y^50 + 6379*y^49 + 8662*y^48 + 34640*y^47 + 38321*y^46 + 18760*y^45 + 13135*y^44 + 15926*y^43 + 34952*y^42 + 28940*y^41 + 13558*y^40 + 42579*y^39 + 38015*y^38 + 33788*y^37 + 12381*y^36 + 195*y^35 + 13709*y^34 + 31500*y^33 + 32994*y^32 + 30486*y^31 + 40414*y^30 + 2578*y^29 + 30525*y^28 + 43067*y^27 + 6195*y^26 + 36288*y^25 + 23236*y^24 + 21493*y^23 + 15808*y^22 + 34500*y^21 + 6390*y^20 + 42994*y^19 + 42151*y^18 + 19248*y^17 + 19291*y^16 + 8124*y^15 + 40161*y^14 + 24726*y^13 + 31874*y^12 + 30272*y^11 + 30761*y^10 + 2296*y^9 + 11017*y^8 + 16559*y^7 + 28949*y^6 + 40499*y^5 + 22377*y^4 + 33628*y^3 + 30598*y^2 + 4386*y + 23814
Ciphertext: 5209*x^176 + 10881*x^175 + 31096*x^174 + 23354*x^173 + 28337*x^172 + 15982*x^171 + 13515*x^170 + 21641*x^169 + 10254*x^168 + 34588*x^167 + 27434*x^166 + 29552*x^165 + 7105*x^164 + 22604*x^163 + 41253*x^162 + 42675*x^161 + 21153*x^160 + 32838*x^159 + 34391*x^158 + 832*x^157 + 720*x^156 + 22883*x^155 + 19236*x^154 + 33772*x^153 + 5020*x^152 + 17943*x^151 + 26967*x^150 + 30847*x^149 + 10306*x^148 + 33966*x^147 + 43255*x^146 + 20342*x^145 + 4474*x^144 + 3490*x^143 + 38033*x^142 + 11224*x^141 + 30565*x^140 + 31967*x^139 + 32382*x^138 + 9759*x^137 + 1030*x^136 + 32122*x^135 + 42614*x^134 + 14280*x^133 + 16533*x^132 + 32676*x^131 + 43070*x^130 + 36009*x^129 + 28497*x^128 + 2940*x^127 + 9747*x^126 + 22758*x^125 + 16615*x^124 + 14086*x^123 + 13038*x^122 + 39603*x^121 + 36260*x^120 + 32502*x^119 + 17619*x^118 + 17700*x^117 + 15083*x^116 + 11311*x^115 + 36496*x^114 + 1300*x^113 + 13601*x^112 + 43425*x^111 + 10376*x^110 + 11551*x^109 + 13684*x^108 + 14955*x^107 + 6661*x^106 + 12674*x^105 + 21534*x^104 + 32132*x^103 + 34135*x^102 + 43684*x^101 + 837*x^100 + 29311*x^99 + 4849*x^98 + 26632*x^97 + 26662*x^96 + 10159*x^95 + 32657*x^94 + 12149*x^93 + 17858*x^92 + 35805*x^91 + 19391*x^90 + 30884*x^89 + 42039*x^88 + 17292*x^87 + 4694*x^86 + 1497*x^85 + 1744*x^84 + 31071*x^83 + 26246*x^82 + 24402*x^81 + 22068*x^80 + 39263*x^79 + 23703*x^78 + 21484*x^77 + 12241*x^76 + 28821*x^75 + 32886*x^74 + 43075*x^73 + 35741*x^72 + 19936*x^71 + 37219*x^70 + 33411*x^69 + 8301*x^68 + 12949*x^67 + 28611*x^66 + 42654*x^65 + 6910*x^64 + 18523*x^63 + 31144*x^62 + 21398*x^61 + 36298*x^60 + 27158*x^59 + 918*x^58 + 38601*x^57 + 4269*x^56 + 5699*x^55 + 36444*x^54 + 34791*x^53 + 37978*x^52 + 32481*x^51 + 8039*x^50 + 11012*x^49 + 11454*x^48 + 30450*x^47 + 1381*x^46 + 32403*x^45 + 8202*x^44 + 8404*x^43 + 37648*x^42 + 43696*x^41 + 34237*x^40 + 36490*x^39 + 41423*x^38 + 35792*x^37 + 36950*x^36 + 31086*x^35 + 38970*x^34 + 12439*x^33 + 7963*x^32 + 16150*x^31 + 11382*x^30 + 3038*x^29 + 20157*x^28 + 23531*x^27 + 32866*x^26 + 5428*x^25 + 21132*x^24 + 13443*x^23 + 28909*x^22 + 42716*x^21 + 6567*x^20 + 24744*x^19 + 8727*x^18 + 14895*x^17 + 28172*x^16 + 30903*x^15 + 26608*x^14 + 27314*x^13 + 42224*x^12 + 42551*x^11 + 37726*x^10 + 11203*x^9 + 36816*x^8 + 5537*x^7 + 20301*x^6 + 17591*x^5 + 41279*x^4 + 7999*x^3 + 33753*x^2 + 34551*x + 9659
输出给了我们三个量,一个是多项式素数最大值,一个是模数多项式,一个是密文多项式。
所以首先分解Modulus
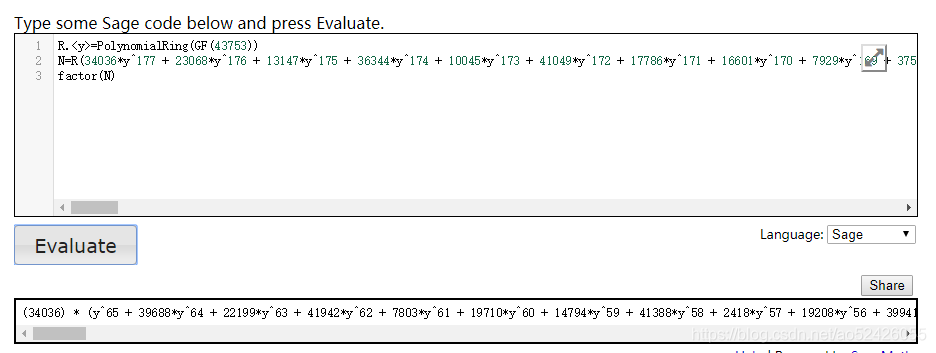
分解N后得到两个多项式。
于是要开始求d
回顾rsa的加密过程,d是e关于φ(n)的唯一逆元,于是转化为求φ(n),而φ(n)在整数中是指与n互质且小于n的数的个数。于是在多项式中应该是与n没有公共多项式的且不高于其幂级的多项是的个数,这样我们很快就可以确认φ(n)的值为(pow(43753,65)-1)*(pow(43753,112)-1)
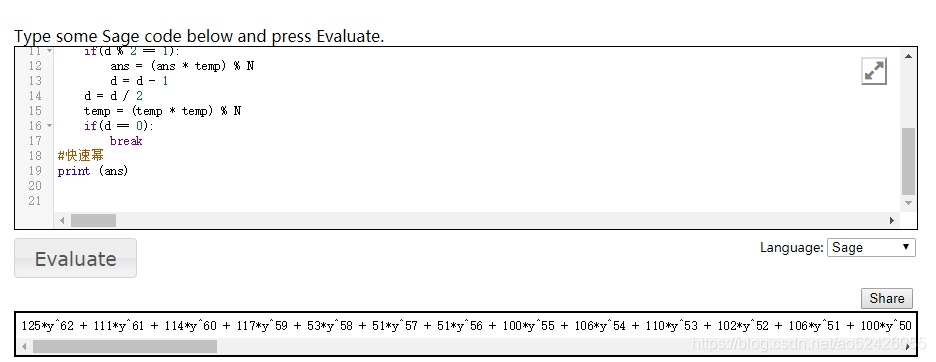
接着就可以用以下脚本求出m
from sage.all import *
R.<y> = PolynomialRing(GF(43753))
N = R("34036*y^177 + 23068*y^176 + 13147*y^175 + 36344*y^174 + 10045*y^173 + 41049*y^172 + 17786*y^171 + 16601*y^170 + 7929*y^169 + 37570*y^168 + 990*y^167 + 9622*y^166 + 39273*y^165 + 35284*y^164 + 15632*y^163 + 18850*y^162 + 8800*y^161 + 33148*y^160 + 12147*y^159 + 40487*y^158 + 6407*y^157 + 34111*y^156 + 8446*y^155 + 21908*y^154 + 16812*y^153 + 40624*y^152 + 43506*y^151 + 39116*y^150 + 33011*y^149 + 23914*y^148 + 2210*y^147 + 23196*y^146 + 43359*y^145 + 34455*y^144 + 17684*y^143 + 25262*y^142 + 982*y^141 + 24015*y^140 + 27968*y^139 + 37463*y^138 + 10667*y^137 + 39519*y^136 + 31176*y^135 + 27520*y^134 + 32118*y^133 + 8333*y^132 + 38945*y^131 + 34713*y^130 + 1107*y^129 + 43604*y^128 + 4433*y^127 + 18110*y^126 + 17658*y^125 + 32354*y^124 + 3219*y^123 + 40238*y^122 + 10439*y^121 + 3669*y^120 + 8713*y^119 + 21027*y^118 + 29480*y^117 + 5477*y^116 + 24332*y^115 + 43480*y^114 + 33406*y^113 + 43121*y^112 + 1114*y^111 + 17198*y^110 + 22829*y^109 + 24424*y^108 + 16523*y^107 + 20424*y^106 + 36206*y^105 + 41849*y^104 + 3584*y^103 + 26500*y^102 + 31897*y^101 + 34640*y^100 + 27449*y^99 + 30962*y^98 + 41434*y^97 + 22125*y^96 + 24314*y^95 + 3944*y^94 + 18400*y^93 + 38476*y^92 + 28904*y^91 + 27936*y^90 + 41867*y^89 + 25573*y^88 + 25659*y^87 + 33443*y^86 + 18435*y^85 + 5934*y^84 + 38030*y^83 + 17563*y^82 + 24086*y^81 + 36782*y^80 + 20922*y^79 + 38933*y^78 + 23448*y^77 + 10599*y^76 + 7156*y^75 + 29044*y^74 + 23605*y^73 + 7657*y^72 + 28200*y^71 + 2431*y^70 + 3860*y^69 + 23259*y^68 + 14590*y^67 + 33631*y^66 + 15673*y^65 + 36049*y^64 + 29728*y^63 + 22413*y^62 + 18602*y^61 + 18557*y^60 + 23505*y^59 + 17642*y^58 + 12595*y^57 + 17255*y^56 + 15316*y^55 + 8948*y^54 + 38*y^53 + 40329*y^52 + 9823*y^51 + 5798*y^50 + 6379*y^49 + 8662*y^48 + 34640*y^47 + 38321*y^46 + 18760*y^45 + 13135*y^44 + 15926*y^43 + 34952*y^42 + 28940*y^41 + 13558*y^40 + 42579*y^39 + 38015*y^38 + 33788*y^37 + 12381*y^36 + 195*y^35 + 13709*y^34 + 31500*y^33 + 32994*y^32 + 30486*y^31 + 40414*y^30 + 2578*y^29 + 30525*y^28 + 43067*y^27 + 6195*y^26 + 36288*y^25 + 23236*y^24 + 21493*y^23 + 15808*y^22 + 34500*y^21 + 6390*y^20 + 42994*y^19 + 42151*y^18 + 19248*y^17 + 19291*y^16 + 8124*y^15 + 40161*y^14 + 24726*y^13 + 31874*y^12 + 30272*y^11 + 30761*y^10 + 2296*y^9 + 11017*y^8 + 16559*y^7 + 28949*y^6 + 40499*y^5 + 22377*y^4 + 33628*y^3 + 30598*y^2 + 4386*y + 23814")
C = R("5209*y^176 + 10881*y^175 + 31096*y^174 + 23354*y^173 + 28337*y^172 + 15982*y^171 + 13515*y^170 + 21641*y^169 + 10254*y^168 + 34588*y^167 + 27434*y^166 + 29552*y^165 + 7105*y^164 + 22604*y^163 + 41253*y^162 + 42675*y^161 + 21153*y^160 + 32838*y^159 + 34391*y^158 + 832*y^157 + 720*y^156 + 22883*y^155 + 19236*y^154 + 33772*y^153 + 5020*y^152 + 17943*y^151 + 26967*y^150 + 30847*y^149 + 10306*y^148 + 33966*y^147 + 43255*y^146 + 20342*y^145 + 4474*y^144 + 3490*y^143 + 38033*y^142 + 11224*y^141 + 30565*y^140 + 31967*y^139 + 32382*y^138 + 9759*y^137 + 1030*y^136 + 32122*y^135 + 42614*y^134 + 14280*y^133 + 16533*y^132 + 32676*y^131 + 43070*y^130 + 36009*y^129 + 28497*y^128 + 2940*y^127 + 9747*y^126 + 22758*y^125 + 16615*y^124 + 14086*y^123 + 13038*y^122 + 39603*y^121 + 36260*y^120 + 32502*y^119 + 17619*y^118 + 17700*y^117 + 15083*y^116 + 11311*y^115 + 36496*y^114 + 1300*y^113 + 13601*y^112 + 43425*y^111 + 10376*y^110 + 11551*y^109 + 13684*y^108 + 14955*y^107 + 6661*y^106 + 12674*y^105 + 21534*y^104 + 32132*y^103 + 34135*y^102 + 43684*y^101 + 837*y^100 + 29311*y^99 + 4849*y^98 + 26632*y^97 + 26662*y^96 + 10159*y^95 + 32657*y^94 + 12149*y^93 + 17858*y^92 + 35805*y^91 + 19391*y^90 + 30884*y^89 + 42039*y^88 + 17292*y^87 + 4694*y^86 + 1497*y^85 + 1744*y^84 + 31071*y^83 + 26246*y^82 + 24402*y^81 + 22068*y^80 + 39263*y^79 + 23703*y^78 + 21484*y^77 + 12241*y^76 + 28821*y^75 + 32886*y^74 + 43075*y^73 + 35741*y^72 + 19936*y^71 + 37219*y^70 + 33411*y^69 + 8301*y^68 + 12949*y^67 + 28611*y^66 + 42654*y^65 + 6910*y^64 + 18523*y^63 + 31144*y^62 + 21398*y^61 + 36298*y^60 + 27158*y^59 + 918*y^58 + 38601*y^57 + 4269*y^56 + 5699*y^55 + 36444*y^54 + 34791*y^53 + 37978*y^52 + 32481*y^51 + 8039*y^50 + 11012*y^49 + 11454*y^48 + 30450*y^47 + 1381*y^46 + 32403*y^45 + 8202*y^44 + 8404*y^43 + 37648*y^42 + 43696*y^41 + 34237*y^40 + 36490*y^39 + 41423*y^38 + 35792*y^37 + 36950*y^36 + 31086*y^35 + 38970*y^34 + 12439*y^33 + 7963*y^32 + 16150*y^31 + 11382*y^30 + 3038*y^29 + 20157*y^28 + 23531*y^27 + 32866*y^26 + 5428*y^25 + 21132*y^24 + 13443*y^23 + 28909*y^22 + 42716*y^21 + 6567*y^20 + 24744*y^19 + 8727*y^18 + 14895*y^17 + 28172*y^16 + 30903*y^15 + 26608*y^14 + 27314*y^13 + 42224*y^12 + 42551*y^11 + 37726*y^10 + 11203*y^9 + 36816*y^8 + 5537*y^7 + 20301*y^6 + 17591*y^5 + 41279*y^4 + 7999*y^3 + 33753*y^2 + 34551*y + 9659")
e = 65537
phi = (43753^65-1)*(43753^112-1)
d = inverse_mod(e, phi)
ans = R("1")
temp= C
while(True):if(d % 2 == 1):ans = (ans * temp) % Nd = d - 1d = d / 2temp = (temp * temp) % Nif(d == 0):break
#快速幂
print (ans)
130.[NPUCTF2020]认清形势,建立信心
查看题目
from Crypto.Util.number import *
from gmpy2 import *
from secret import flagp = getPrime(25)
e = # Hidden
q = getPrime(25)
n = p * q
m = bytes_to_long(flag.strip(b"npuctf{").strip(b"}"))c = pow(m, e, n)
print(c)
print(pow(2, e, n))
print(pow(4, e, n))
print(pow(8, e, n))'''
169169912654178
128509160179202
518818742414340
358553002064450
'''
首先,这里展开一个公式:
((a mod x) ^ b) mod x = (a ^ b) mod x
作为小白,接下来是推导证明:
设 a = kx + d
(a mod x) ^ b = d ^ b
a ^ b = (kx + d) ^ b,此处二项式展开得知共b+1项 前b项都有x这个因数 最后一个为d ^ b.
则根据题目,
2 ^ e mod n = a
4 ^ e mod n = 2 ^ 2e mod n = (2 ^ e mod n) ^ 2 mod n = a ^ 2 mod n = b
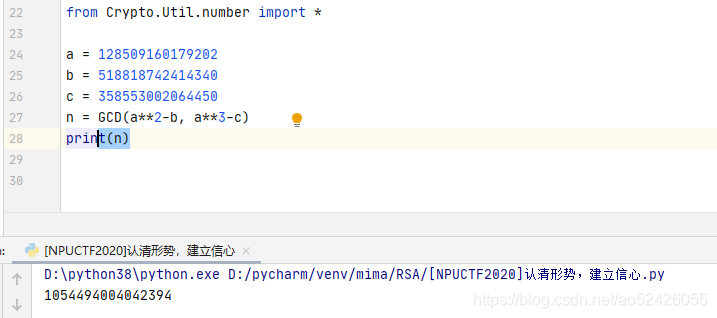
a ^ 2 - b = kn(k=1,k=2…) 同理,a ^ 3 - c = kn(k=1,k=2…). n为两式的公因数,由此根据gcd( a ^ 2 - b,a ^ 3 - c)求出n
把N分解
把2去掉 这就是pq了
然后就是求e
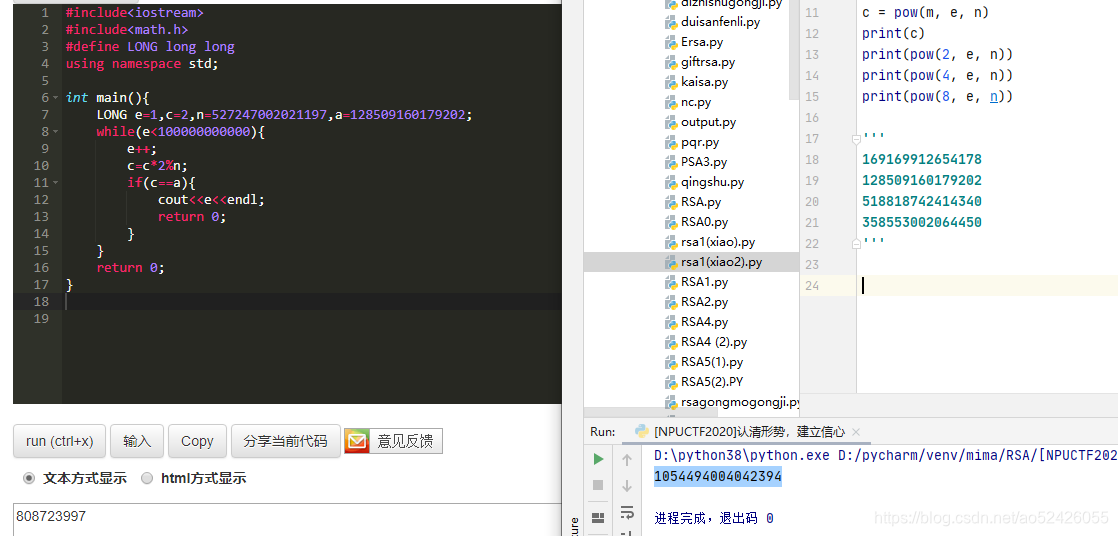
这样epqc就都有了就正常写入就行了
'''from Crypto.Util.number import *
from gmpy2 import *
from secret import flagp = getPrime(25)
e = # Hidden
q = getPrime(25)
n = p * q
m = bytes_to_long(flag.strip(b"npuctf{").strip(b"}"))c = pow(m, e, n)
print(c)
print(pow(2, e, n))
print(pow(4, e, n))
print(pow(8, e, n))169169912654178
128509160179202
518818742414340
358553002064450
'''
'''from Crypto.Util.number import *a = 128509160179202
b = 518818742414340
c = 358553002064450
n = GCD(a**2-b, a**3-c)
print(n)
'''
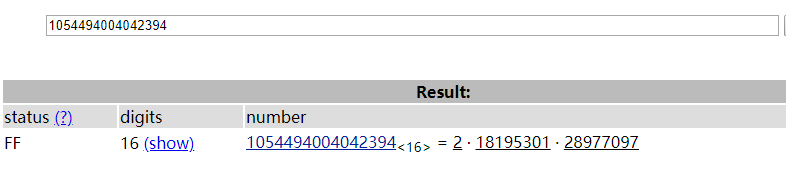
from Crypto.Util.number import *
from gmpy2 import *e = 808723997
p = 18195301
q = 28977097
c = 169169912654178
m = pow(c,invert(e,(p-1)*(q-1)),p*q)
flag = long_to_bytes(m)
print (flag)当然用以前写的脚本也是可以的
131.[AFCTF2018]MagicNum
查看题目
132.[AFCTF2018]Tiny LFSR
这题看起来特别的麻烦,我们先来一步步分析。题目用同一个加密脚本加密了两份文件,一份是plain加密得到的cipher,另一个是flag加密得到的flagencode,再看看加密的方式,前一部分是通过lfsr的密钥key与plain前一部分按位异或得到的,后一部分是通过,lfsr生成的密钥流与plain的后一部分按位异或得到的,感觉就是特别的繁琐了。于是,我们的思路是先通过cipher与plain按位异或得到key值先,然后我们可以知道LFSR中的key与mask位数是相同的,看了一下mask的位数是二进制64位,那么key的位数就是16进制16位,也就是8位ASCII字符,于是我们设置异或的长度为8个字符,当然也可以设置更多
cipher="72472201E3C0AC877A27C18729749FDA185C1DF902500AEB425C5B6A53574B4A00508546094A90A2F1547780FD401E8C2983A70F22931F0BCC0EBE6EC83B1284BF2023AEBE59B1CBD2D9C395E9C76D42DF65C470C23C92E65F66504F3025B5F660E772096A172CDD"
c=cipher.decode('hex')
#print c
plain="sdgfjkahblskdjxbvfskljdfbguisldfbvghkljsdfbghsjkldhbgjklsdbgvlkjsdgbkljb sdkljfhwelo;sdfghioeurthgbnjl k"
a=""
for i in range(0, 8):a+=chr(ord(c[i])^ord(plain[i]))
print a通过这样即可得到密钥key,也可以带入原脚本验证
cipher="72472201E3C0AC877A27C18729749FDA185C1DF902500AEB425C5B6A53574B4A00508546094A90A2F1547780FD401E8C2983A70F22931F0BCC0EBE6EC83B1284BF2023AEBE59B1CBD2D9C395E9C76D42DF65C470C23C92E65F66504F3025B5F660E772096A172CDD"
c=cipher.decode('hex')
#print c
plain="sdgfjkahblskdjxbvfskljdfbguisldfbvghkljsdfbghsjkldhbgjklsdbgvlkjsdgbkljb sdkljfhwelo;sdfghioeurthgbnjl k"
a=""
for i in range(0, 8):a+=chr(ord(c[i])^ord(plain[i]))
print a可以发现与给的cipher的后一部分相同,可以认为得到的key是正确的,于是我们可以生成lfsr产生的密钥流,生成位数设置位flagencode的位数
R = bytes_to_long(a)
tmptext=""
#for i in range(len(a), len(plain)):
for i in range(len(a), 1213):tmp=0for j in range(8):(R,out)=lfsr(R,mask)tmp=(tmp << 1)^outtmptext+=chr(tmp)
print 2,tmptext这里要注意,一定要初始话R的值
于是我们可以开始求解flag,先将前一部分与key按位异或
flagencode1="484D6504E6C6BD9A6C22DC8B613E8698025300F70F4843EB455E4A614158440C114E8B48160688B4F25B6693F04154CF09A19C3F6CD91D149F0BFC7AD63E1F9AEC3621ABBC46AFCC808AD096EADE6E0AC16ED86A8D6F94E94C2E50537531E7EE61EE7506725B6AC3BBE2C1886B8B9B6FECB4464F1778D57F0729924FBED5B7D9E581120E95BC75564B40DF37C57DFD152D7163FD61E12DD86347FD55EB3FB994818E61AF3845FB59D2A1633105606FF861F4809934AC6994B4A09EA57629C816C4F3A7C159BCCEF293534D3EFFFFF4AA9CB87E5E37D7292FE20C15F9A282859C93F0190F9DA409A125D47BCD80E39EE103DDA17498B5EF7EED50A064F2A5A78C8BDB69CDE2855F75752460AE0346E1716274BE3D2A733107927ACE7B3B3CD86AB5F4FB3AA52A3B5ADAE1A603B4C97C04067EA64785C243634382B6C66066F09A58FC4F381FB656E8C423041D338738E52CE9E816BCDFFD7BB2F02F90ACDDB76DF2E3E9861B40520DA20670A341A88CD9D1AA37B17F03672D424A8FB3BF01E2CAEE32F6A9F871AA0CA0BA999F4659FC0A4506FB64C910610F0DBEFFCBCA04AD81A96608ED9BDE070A2BF48982D82BDFE096F8FFAA2824F66B3E5DA04DAC0F985CF571EBDB14B3A99EEC5F861129D62EA28310D0F7F1FC5F09D5BAB601961E38BD9F0151175F71421BBFFCDD19FAFA4047CA27EF6C74C351CDF73F02457E682AE6370C1BC2E3DC9AD8EC0C45D2B011657ABEBDEE68BEA83453CAF5B13D999BB706A44A1D69EA1E43049D1219CBF433A4668E0750ECEC29874A904525DAA518F0247B13AF5571DB7E97F5CECD0E0B082F6EEF736A96ECC30F69B12B94289FF597E643DC5DBF54E1393E9DBF70981867845FA58351B07F1A891FDEFA69CB9CF50F803E7961B9E8F0D89C5F698269B28C32588F5E0229CB75E8135AE3E4A2F59C8F314A1041D629A4FD6CC2D1603AE7B866258FED3740EBC8305203972AF3BB89E64D34248162A36CCB1288AD7380914507C95894842B8A4780659D5A31992E6BDCCDD6D2C60D3A1B0B90A382B7BEC2F4F2E5C1A1A2B03D45E0A0F2B091C37D5869F0E7483C7575A12F551261D6B326E6FB4B59B604234D36BC35050A608D738C31AD5F18EC82364B9C41000F511274443F5A8F02DCF901CC0874C06567296598CA6BD5DAF357F4C5F01A8C555C4DE796315FB9B5C5C43DB2C0E4D4E32A5B26DA45E28EABDF5575B4F16445197C7A9E93C89B4C7DDBA31E117D8ADFE342CE6518B32F9E24F974829B8DAF0F07C1BAE2DB64D390DB5DBBC765D075270198B3F788A2DA30CCAED2D6658108C7593ACFE65B9A98FB9E156C2E6921B7E9A7555DFF69744433EBACA2C02BC8BF3C9DE7DC5BCB04C3504D25F285A70D0B0ED17A0AFFB776ACA2958B8B1009DC4ECDF74159E3C192041CB85ED364381A21881579A4DEBC4C1585C9803B117D6D8C16C984743FBC9A220D3C15014407D716068DC6520096FC4FA734E65EBACB00EFE7A737400CB815EE2BD6948C8186651EDA7D5D5397D27E0F1851CCED80E0D752F9BFF4D7DC3CA1441611BEA3297FB6FAFFEBD18B15D6456A408D5E6217E31F0D375CA6CE5F799DE9C177800EFC622BE9060982D23DC6857B79A1178FC03CD6FC2EC7CB91D8F3277ABA86F5F02AFD1428A6D4B595D0359A28C74EBD4EEEE7DD6C9C9BE9C71420E9D4277EED4F474A21D39C02734581"
flagencode2=flagencode1.decode('hex')
print len(flagencode2)
#print flagencode2
flag=""
for i in range(0, 8):flag+=chr(ord(a[i])^ord(flagencode2[i]))
print flag
#In compu后半部分通过将flagencrypt与密钥流按位异或即可,整题脚本给出
import os,random,sys,string
from hashlib import sha256
import gmpy2
from Crypto.Util.number import *
import base64
mask = 0b1101100000000000000000000000000000000000000000000000000000000000
cipher="72472201E3C0AC877A27C18729749FDA185C1DF902500AEB425C5B6A53574B4A00508546094A90A2F1547780FD401E8C2983A70F22931F0BCC0EBE6EC83B1284BF2023AEBE59B1CBD2D9C395E9C76D42DF65C470C23C92E65F66504F3025B5F660E772096A172CDD"
c=cipher.decode('hex')
#print c
plain="sdgfjkahblskdjxbvfskljdfbguisldfbvghkljsdfbghsjkldhbgjklsdbgvlkjsdgbkljb sdkljfhwelo;sdfghioeurthgbnjl k"
a=""
for i in range(0, 8):a+=chr(ord(c[i])^ord(plain[i]))
print adef lfsr(R, mask):output = (R << 1) & 0xffffffffffffffffi=(R&mask)&0xfffffffffffffffflastbit=0while i!=0:lastbit^=(i&1)i=i>>1output^=lastbitreturn (output,lastbit)R = bytes_to_long(a)
t=""
for i in range(len(a), len(plain)):tmp=0for j in range(8):(R,out)=lfsr(R,mask)tmp=(tmp << 1)^outt+=long_to_bytes((tmp^ord(plain[i])))
print 1,tR = bytes_to_long(a)
tmptext=""
#for i in range(len(a), len(plain)):
for i in range(len(a), 1213):tmp=0for j in range(8):(R,out)=lfsr(R,mask)tmp=(tmp << 1)^outtmptext+=chr(tmp)
print 2,tmptextflagencode1="484D6504E6C6BD9A6C22DC8B613E8698025300F70F4843EB455E4A614158440C114E8B48160688B4F25B6693F04154CF09A19C3F6CD91D149F0BFC7AD63E1F9AEC3621ABBC46AFCC808AD096EADE6E0AC16ED86A8D6F94E94C2E50537531E7EE61EE7506725B6AC3BBE2C1886B8B9B6FECB4464F1778D57F0729924FBED5B7D9E581120E95BC75564B40DF37C57DFD152D7163FD61E12DD86347FD55EB3FB994818E61AF3845FB59D2A1633105606FF861F4809934AC6994B4A09EA57629C816C4F3A7C159BCCEF293534D3EFFFFF4AA9CB87E5E37D7292FE20C15F9A282859C93F0190F9DA409A125D47BCD80E39EE103DDA17498B5EF7EED50A064F2A5A78C8BDB69CDE2855F75752460AE0346E1716274BE3D2A733107927ACE7B3B3CD86AB5F4FB3AA52A3B5ADAE1A603B4C97C04067EA64785C243634382B6C66066F09A58FC4F381FB656E8C423041D338738E52CE9E816BCDFFD7BB2F02F90ACDDB76DF2E3E9861B40520DA20670A341A88CD9D1AA37B17F03672D424A8FB3BF01E2CAEE32F6A9F871AA0CA0BA999F4659FC0A4506FB64C910610F0DBEFFCBCA04AD81A96608ED9BDE070A2BF48982D82BDFE096F8FFAA2824F66B3E5DA04DAC0F985CF571EBDB14B3A99EEC5F861129D62EA28310D0F7F1FC5F09D5BAB601961E38BD9F0151175F71421BBFFCDD19FAFA4047CA27EF6C74C351CDF73F02457E682AE6370C1BC2E3DC9AD8EC0C45D2B011657ABEBDEE68BEA83453CAF5B13D999BB706A44A1D69EA1E43049D1219CBF433A4668E0750ECEC29874A904525DAA518F0247B13AF5571DB7E97F5CECD0E0B082F6EEF736A96ECC30F69B12B94289FF597E643DC5DBF54E1393E9DBF70981867845FA58351B07F1A891FDEFA69CB9CF50F803E7961B9E8F0D89C5F698269B28C32588F5E0229CB75E8135AE3E4A2F59C8F314A1041D629A4FD6CC2D1603AE7B866258FED3740EBC8305203972AF3BB89E64D34248162A36CCB1288AD7380914507C95894842B8A4780659D5A31992E6BDCCDD6D2C60D3A1B0B90A382B7BEC2F4F2E5C1A1A2B03D45E0A0F2B091C37D5869F0E7483C7575A12F551261D6B326E6FB4B59B604234D36BC35050A608D738C31AD5F18EC82364B9C41000F511274443F5A8F02DCF901CC0874C06567296598CA6BD5DAF357F4C5F01A8C555C4DE796315FB9B5C5C43DB2C0E4D4E32A5B26DA45E28EABDF5575B4F16445197C7A9E93C89B4C7DDBA31E117D8ADFE342CE6518B32F9E24F974829B8DAF0F07C1BAE2DB64D390DB5DBBC765D075270198B3F788A2DA30CCAED2D6658108C7593ACFE65B9A98FB9E156C2E6921B7E9A7555DFF69744433EBACA2C02BC8BF3C9DE7DC5BCB04C3504D25F285A70D0B0ED17A0AFFB776ACA2958B8B1009DC4ECDF74159E3C192041CB85ED364381A21881579A4DEBC4C1585C9803B117D6D8C16C984743FBC9A220D3C15014407D716068DC6520096FC4FA734E65EBACB00EFE7A737400CB815EE2BD6948C8186651EDA7D5D5397D27E0F1851CCED80E0D752F9BFF4D7DC3CA1441611BEA3297FB6FAFFEBD18B15D6456A408D5E6217E31F0D375CA6CE5F799DE9C177800EFC622BE9060982D23DC6857B79A1178FC03CD6FC2EC7CB91D8F3277ABA86F5F02AFD1428A6D4B595D0359A28C74EBD4EEEE7DD6C9C9BE9C71420E9D4277EED4F474A21D39C02734581"
flagencode2=flagencode1.decode('hex')
print len(flagencode2)
#print flagencode2
flag=""
for i in range(0, 8):flag+=chr(ord(a[i])^ord(flagencode2[i]))
print flag
#In compufor i in range(len(a), 1213):flag+=long_to_bytes(ord(tmptext[i-len(a)])^ord(flagencode2[i]))
print 3,flag
#3 In computing, a linear-feedback shift register (LFSR) is a shift register whose input bit is a linear function of its previous state.#The most commonly used linear function of single bits is exclusive-or (XOR). Thus, an LFSR is most often a shift register whose input bit is driven by the XOR of some bits of the overall shift register value.#The initial value of the LFSR is called the seed, and because the operation of the register is deterministic, the stream of values produced by the register is completely determined by its current (or previous) state. Likewise, because the register has a finite number of possible states, it must eventually enter a repeating cycle. However, an LFSR with a well-chosen feedback function can produce a sequence of bits that appears random and has a very long cycle.#Applications of LFSRs include generating pseudo-random numbers, pseudo-noise sequences, fast digital counters, and whitening sequences. Both hardware and software implementations of LFSRs are common.#The mathematics of a cyclic redundancy check, used to provide a quick check against transmission errors, are closely related to those of an LFSR.#Congratulations! flag is afctf{read_is_hard_but_worthy}
这道题是看的大佬的wp
133.[AFCTF2018]One Secret, Two encryption
查看题目
两个pub后缀的用010打开是两个公钥加密
得到两个n,e
从这个猜一手,有公共素数gmpy2.gcd(n1,n2)求得一个公共素数就很简单了
import gmpy2
from Crypto.Util.number import *
n1=4850297138162223468826481623082440249579136876798312652735204698689613969008632545220976699170308454082390834742570718247804202060929493571642074679428565168405877110681518105667301785653517697684490982375078989886040451115082120928982588380914609273008153977907950532498605486225883973643141516024058315360572988744607134110254489421516026937249163493982681336628726033489124705657217768229058487155865265080427488028921879608338898933540825564889012166181346177276639828346376362168934208822467295673761876965864573164529336885250577357767314256581019474130651412100897839606491189424373959244023695669653213498329
n2=2367536768672000959668181171787295271898789288397672997134843418932405959946739637368044420319861797856771490573443003520137149324080217971836780570522258661419034481514883068092752166752967879497095564732505614751532330408675056285275354250157955321457579006360393218327164804951384290041956551855334492796719901818165788902547584563455747941517296875697241841177219635024461395596117584194226134777078874543699117761893699634303571421106917894215078938885999963580586824497040073241055890328794310025879014294051230590716562942538031883965317397728271589759718376073414632026801806560862906691989093298478752580277
e1=1666626632960368239001159408047765991270250042206244157447171188195657302933019501932101777999510001235736338843107709871785906749393004257614129802061081155861433722380145001537181142613515290138835765236002811689986472280762408157176437503021753061588746520433720734608953639111558556930490721517579994493088551013050835690019772600744317398218183883402192060480979979456469937863257781362521184578142129444122428832106721725409309113975986436241662107879085361014650716439042856013203440242834878648506244428367706708431121109714505981728529818874621868624754285069693368779495316600601299037277003994790396589299
e2=65537
p=gmpy2.gcd(n1,n2)
q=n2//p
assert(p*q==n2)
phi=(p-1)*(q-1)
d=gmpy2.invert(e2,phi)
c_bytes=open("flag_encry2","rb").read()
c=bytes_to_long(c_bytes)
m=pow(c,d,n2)
flag=long_to_bytes(m)
print(flag)
用这个也可以,或者直接用
运行得到b'\x02~\x83\xa7\xed\xd5\xde\xf1\xb8\xc6\x17%5:\xf7wZn\xc2WbDn)\x070\xfc\x98}\xa5\x96@\x90?Y\xba\xe5\xca\xdam\xbaGF\tz\xe7W\xcd\x94\x1c#\xecti\x8b\x89\x18hH\xc5\xbf\x10\xe983C}3Cz>HbX\xbe\x98<JG\x86??\xe2?\xfc\xaf\xb60\xbe\xec\xe3h\x07\xda\xea\xefSw\xb1t\x9bp\x03y\x12\xf2<\x99\xae\xf6\xde\x9b\xdf\xdd\xb4\xf7\x88t\xe0\xff% \x11"B\xa7r\xf2}\xf3\xaf\xca\x9dfI.\x08\xd2\xdb1\x18E\xed\xb38\xe5\xcc\xc3#\x1eT*\xec\xc4a\x95\xd9\xd9\xe7\xd4\x88O\xa3\'\xae9S\xa3\xd1\x7f~+\xefqa\xe1y\x82\x19l\x8a\x8b\xc5\xe8\xc1\xbd\t\x88\xbf+Th\xba\x8f\xfd\xb0\x89\n\x92\x00OpenSSL is widely used\r\nflag is afctf{You_Know_0p3u55I}'
134.[NCTF2019]easyRSA
查看题目
from flag import flage = 0x1337
p = 199138677823743837339927520157607820029746574557746549094921488292877226509198315016018919385259781238148402833316033634968163276198999279327827901879426429664674358844084491830543271625147280950273934405879341438429171453002453838897458102128836690385604150324972907981960626767679153125735677417397078196059
q = 112213695905472142415221444515326532320352429478341683352811183503269676555434601229013679319423878238944956830244386653674413411658696751173844443394608246716053086226910581400528167848306119179879115809778793093611381764939789057524575349501163689452810148280625226541609383166347879832134495444706697124741
n = p * qassert(flag.startswith('NCTF'))
m = int.from_bytes(flag.encode(), 'big')
assert(m.bit_length() > 1337)c = pow(m, e, n)
print(c)
# 10562302690541901187975815594605242014385201583329309191736952454310803387032252007244962585846519762051885640856082157060593829013572592812958261432327975138581784360302599265408134332094134880789013207382277849503344042487389850373487656200657856862096900860792273206447552132458430989534820256156021128891296387414689693952047302604774923411425863612316726417214819110981605912408620996068520823370069362751149060142640529571400977787330956486849449005402750224992048562898004309319577192693315658275912449198365737965570035264841782399978307388920681068646219895287752359564029778568376881425070363592696751183359
眨眼一看pqec都有了还在想这么简单的题,结果啪啪打脸,没办法逆元
然后我就想用c=pow(m,e,n)来解嗯事实好像能解,当时我没运行出来,后面我就去找大佬wp
正常情况下的RSA都要求e和phi(n)要互素,不过也有一些e和phi(n)有很小的公约数的题目,这些题目基本都能通过计算e对phi(n)的逆元d来求解。
然而本题则为e和p-1(或q-1)的最大公约数就是e本身,也就是说e | p-1,只有对c开e次方根才行。
可以将同余方程
m^e \equiv c \quad (\text{mod}\ n)
化成
\begin{aligned}
m^e &\equiv c \quad (\text{mod}\ p)\newline
m^e &\equiv c \quad (\text{mod}\ q)
\end{aligned}
然后分别在GF§和GF(q)上对c开e=0x1337次方根,再用CRT组合一下即可得到在mod n下的解。
问题是,如何在有限域内开根?
这里e与p-1和q-1都不互素,不能简单地求个逆元就完事。
这种情况下,开平方根可以用Tonelli–Shanks algorithm,wiki说这个算法可以扩展到开n次方根。
在这篇paper里给出了具体的算法:Adleman-Manders-Miller rth Root Extraction Method
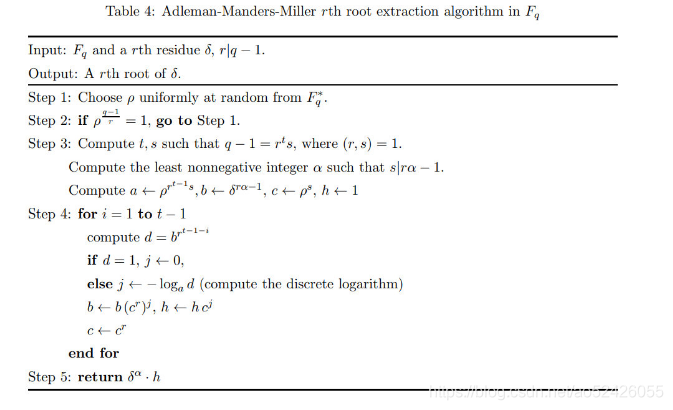
这个算法只能开出一个根,实际上开0x1337次方,最多会有0x1337个根(这题的情况下有0x1337个根)。如何找到所有的primitve 0x1337th root of 1?
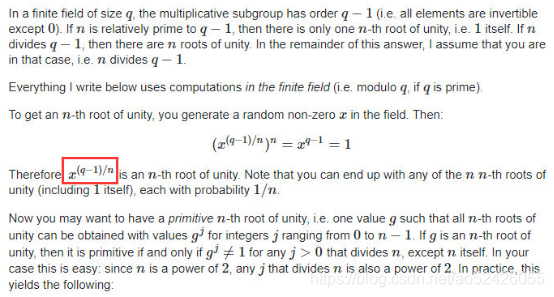
先用Adleman-Manders-Miller rth Root Extraction Method在GF§和GF(q)上对c开e次根,分别得到一个解。大概不到10秒。
然后去找到所有的0x1336个primitive nth root of 1,乘以上面那个解,得到所有的0x1337个解。大概1分钟。
再用CRT对GF§和GF(q)上的两组0x1337个解组合成mod n下的解,可以得到0x1337**2==24196561个mod n的解。最后能通过check的即为flag。大概十几分钟。
exp.sage如下
import random
import time# About 3 seconds to run
def AMM(o, r, q):start = time.time()print('\n----------------------------------------------------------------------------------')print('Start to run Adleman-Manders-Miller Root Extraction Method')print('Try to find one {:#x}th root of {} modulo {}'.format(r, o, q))g = GF(q)o = g(o)p = g(random.randint(1, q))while p ^ ((q-1) // r) == 1:p = g(random.randint(1, q))print('[+] Find p:{}'.format(p))t = 0s = q - 1while s % r == 0:t += 1s = s // rprint('[+] Find s:{}, t:{}'.format(s, t))k = 1while (k * s + 1) % r != 0:k += 1alp = (k * s + 1) // rprint('[+] Find alp:{}'.format(alp))a = p ^ (r**(t-1) * s)b = o ^ (r*alp - 1)c = p ^ sh = 1for i in range(1, t):d = b ^ (r^(t-1-i))if d == 1:j = 0else:print('[+] Calculating DLP...')j = - dicreat_log(a, d)print('[+] Finish DLP...')b = b * (c^r)^jh = h * c^jc = c ^ rresult = o^alp * hend = time.time()print("Finished in {} seconds.".format(end - start))print('Find one solution: {}'.format(result))return resultdef findAllPRoot(p, e):print("Start to find all the Primitive {:#x}th root of 1 modulo {}.".format(e, p))start = time.time()proot = set()while len(proot) < e:proot.add(pow(random.randint(2, p-1), (p-1)//e, p))end = time.time()print("Finished in {} seconds.".format(end - start))return prootdef findAllSolutions(mp, proot, cp, p):print("Start to find all the {:#x}th root of {} modulo {}.".format(e, cp, p))start = time.time()all_mp = set()for root in proot:mp2 = mp * root % passert(pow(mp2, e, p) == cp)all_mp.add(mp2)end = time.time()print("Finished in {} seconds.".format(end - start))return all_mpc = 10562302690541901187975815594605242014385201583329309191736952454310803387032252007244962585846519762051885640856082157060593829013572592812958261432327975138581784360302599265408134332094134880789013207382277849503344042487389850373487656200657856862096900860792273206447552132458430989534820256156021128891296387414689693952047302604774923411425863612316726417214819110981605912408620996068520823370069362751149060142640529571400977787330956486849449005402750224992048562898004309319577192693315658275912449198365737965570035264841782399978307388920681068646219895287752359564029778568376881425070363592696751183359
p = 199138677823743837339927520157607820029746574557746549094921488292877226509198315016018919385259781238148402833316033634968163276198999279327827901879426429664674358844084491830543271625147280950273934405879341438429171453002453838897458102128836690385604150324972907981960626767679153125735677417397078196059
q = 112213695905472142415221444515326532320352429478341683352811183503269676555434601229013679319423878238944956830244386653674413411658696751173844443394608246716053086226910581400528167848306119179879115809778793093611381764939789057524575349501163689452810148280625226541609383166347879832134495444706697124741
e = 0x1337
cp = c % p
cq = c % q
mp = AMM(cp, e, p)
mq = AMM(cq, e, q)
p_proot = findAllPRoot(p, e)
q_proot = findAllPRoot(q, e)
mps = findAllSolutions(mp, p_proot, cp, p)
mqs = findAllSolutions(mq, q_proot, cq, q)
print mps, mqsdef check(m):h = m.hex()if len(h) & 1:return Falseif h.decode('hex').startswith('NCTF'):print(h.decode('hex'))return Trueelse:return False# About 16 mins to run 0x1337^2 == 24196561 times CRT
start = time.time()
print('Start CRT...')
for mpp in mps:for mqq in mqs:solution = CRT_list([int(mpp), int(mqq)], [p, q])if check(solution):print(solution)print(time.time() - start)end = time.time()
print("Finished in {} seconds.".format(end - start))
好像少了一个括号,这是我改之前的
运行的到flag{T4k31ng_Ox1337_r00t_1s_n0t_th4t_34sy}
135.[NPUCTF2020]共 模 攻 击
查看题目
from gmpy2 import *
from Crypto.Util.number import *
from secret import flagflag = flag.strip(b"npuctf{").strip(b"}")
m = bytes_to_long(flag)p, q = getPrime(512), getPrime(512)
n = p * q
e1, e2 = p, q
c1, c2 = pow(m, e1, n), pow(m, e2, n)print(n)
print(c1)
print(c2)128205304743751985889679351195836799434324346996129753896234917982647254577214018524580290192396070591032007818847697193260130051396080104704981594190602854241936777324431673564677900773992273463534717009587530152480725448774018550562603894883079711995434332008363470321069097619786793617099517770260029108149
96860654235275202217368130195089839608037558388884522737500611121271571335123981588807994043800468529002147570655597610639680977780779494880330669466389788497046710319213376228391138021976388925171307760030058456934898771589435836261317283743951614505136840364638706914424433566782044926111639955612412134198
9566853166416448316408476072940703716510748416699965603380497338943730666656667456274146023583837768495637484138572090891246105018219222267465595710692705776272469703739932909158740030049375350999465338363044226512016686534246611049299981674236577960786526527933966681954486377462298197949323271904405241585
from gmpy2 import *
from Crypto.Util.number import *
from secret import hintm = bytes_to_long(hint)
p = getPrime(256)
c = pow(m, 256, p)
print(p)p, q = getPrime(256), getPrime(256)
n = p * q
e1, e2 = getPrime(32), getPrime(32)
c1, c2 = pow(c, e1, n), pow(c, e2, n)
print(n)
print(e1, c1)
print(e2, c2)107316975771284342108362954945096489708900302633734520943905283655283318535709
6807492006219935335233722232024809784434293293172317282814978688931711423939629682224374870233587969960713638310068784415474535033780772766171320461281579
2303413961 1754421169036191391717309256938035960912941109206872374826444526733030696056821731708193270151759843780894750696642659795452787547355043345348714129217723
2622163991 1613454015951555289711148366977297613624544025937559371784736059448454437652633847111272619248126613500028992813732842041018588707201458398726700828844249我写的笔记有点乱

解密脚本
from gmpy2 import*
from libnum import*
from sympy import*p = 107316975771284342108362954945096489708900302633734520943905283655283318535709e1 = 2303413961
c1 = 1754421169036191391717309256938035960912941109206872374826444526733030696056821731708193270151759843780894750696642659795452787547355043345348714129217723e2 = 2622163991
c2 = 1613454015951555289711148366977297613624544025937559371784736059448454437652633847111272619248126613500028992813732842041018588707201458398726700828844249
n = 6807492006219935335233722232024809784434293293172317282814978688931711423939629682224374870233587969960713638310068784415474535033780772766171320461281579s = gcdext(e1,e2)
c = pow(c1,s[1],n)*pow(c2,s[2],n) % n
print(c)
#c = 19384002358725759679198917686763310349050988223627625096050800369760484237557
m = nthroot_mod(c,256,p)
print(n2s(m))
hiti得到一个m.bit_length() < 400
from gmpy2 import*
from libnum import*
from Crypto.Util.number import*n = 128205304743751985889679351195836799434324346996129753896234917982647254577214018524580290192396070591032007818847697193260130051396080104704981594190602854241936777324431673564677900773992273463534717009587530152480725448774018550562603894883079711995434332008363470321069097619786793617099517770260029108149
c1 = 96860654235275202217368130195089839608037558388884522737500611121271571335123981588807994043800468529002147570655597610639680977780779494880330669466389788497046710319213376228391138021976388925171307760030058456934898771589435836261317283743951614505136840364638706914424433566782044926111639955612412134198
c2 = 9566853166416448316408476072940703716510748416699965603380497338943730666656667456274146023583837768495637484138572090891246105018219222267465595710692705776272469703739932909158740030049375350999465338363044226512016686534246611049299981674236577960786526527933966681954486377462298197949323271904405241585a = c1+c2
b = c1*c2print(a)
print(b)
#中间 Sage 求 m 的代码:
#a = 106427507401691650533776606268030543324548306805584488340881108460215302001780649045082140067384306297497785054794169701530927082798998717147796265177082494273319180022953309137549878052025764276170773098393102683446915458123682447310617265418188192465923366892572673596378919944244343124060963227516817375783
#b = 926651656671911333597022401968870409343942400492881255142377951759176631494915016941991504123810265329862246592861145719213675502795378053564904818765377025096483601036025012267103260702787555612216755188521913405305861451125814149409508425602231670292131422273268728629782633354498648021859614223672123489318899205627785426402597996319440198218774038390809403281952702730883306007226797632389267386912707857093556335846269954270572920361347019614365402744026533713442449916555425678184406380167614011131702418493073759816310890056281917310110034453007210415242707924141697749818907383248545179118594511927630223830
#n = 128205304743751985889679351195836799434324346996129753896234917982647254577214018524580290192396070591032007818847697193260130051396080104704981594190602854241936777324431673564677900773992273463534717009587530152480725448774018550562603894883079711995434332008363470321069097619786793617099517770260029108149
#R.<x>=Zmod(n)[]
#f = x^2 - a*x +b
#f.small_roots(X=2^400) #根的绝对边界,根就是flag
m=4242839043019782000788118887372132807371568279472499477998758466224002905442227156537788110520335652385855
print(hex(m))#转换十六进制
print(bytes.fromhex(hex(m)[2:]))#ascll码
那个sage代码也给了m使用sgae求出来的
最终flag就是verrrrrrry_345yyyyyyy_rsaaaaaaa_righttttttt?
136.[XNUCA2018]Warmup
查看题目
打开流量包。
通过分析一共有6个流。发现Alice和Dave的n相同,于是可以采用共模攻击。
n=25118186052801903419891574512806521370646053661385577314262283167479853375867074736882903917202574957661470179148882538361560784362740207649620536746860883395110443930778132343642295247749797041449601967434690280754279589691669366595486824752597992245067619256368446164574344449914827664991591873150416287647528776014468498025993455819767004213726389160036077170973994848480739499052481386539293425983093644799960322581437734560001018025823047877932105216362961838959964371333287407071080250979421489210165485908404019927393053325809061787560294489911475978342741920115134298253806238766543518220987363050115050813263
e1=7669
c1=22917655888781915689291442748409371798632133107968171254672911561608350738343707972881819762532175014157796940212073777351362314385074785400758102594348355578275080626269137543136225022579321107199602856290254696227966436244618441350564667872879196269074433751811632437228139470723203848006803856868237706401868436321225656126491701750534688966280578771996021459620472731406728379628286405214996461164892486734170662556518782043881759918394674517409304629842710180023814702447187081112856416034885511215626693534876901484105593275741829434329109239483368867518384522955176807332437540578688867077569728548513876841471
e2=6947
c2=20494665879116666159961016125949070097530413770391893858215547229071116025581822729798313796823204861624912909030975450742122802775879194445232064367771036011021366123393917354134849911675307877324103834871288513274457941036453477034798647182106422619504345055259543675752998330786906376830335403339610903547255965127196315113331300512641046933227008101401416026809256813221480604662012101542846479052832128788279031727880750642499329041780372405567816904384164559191879422615238580181357183882111249939492668328771614509476229785062819586796660370798030562805224704497570446844131650030075004901216141893420140140568
import gmpy2
import binascii
import rsa
import math
def exgcd(m, n, x, y):if n == 0:x = 1y = 0return (m, x, y)a1 = b = 1a = b1 = 0c = md = nq = int(c / d)r = c % dwhile r:c = dd = rt = a1a1 = aa = t - q * at = b1b1 = bb = t - q * bq = int(c / d)r = c % dx = ay = breturn (d, x, y)#扩展欧几里得算法
ans=exgcd(e1,e2,0,0)
s1=ans[1]
s2=ans[2]
m=(gmpy2.powmod(c1,s1,n)*gmpy2.powmod(c2,s2,n))%n
print(binascii.unhexlify(hex(m)[2:]))
运行得到b'FLAG{g00d_Luck_&_Hav3_Fun}'
137.[AFCTF2018]MyOwnCBC
查看题目
#!/usr/bin/python2.7
# -*- coding: utf-8 -*-from Crypto.Cipher import AES
from Crypto.Random import random
from Crypto.Util.number import long_to_bytesdef MyOwnCBC(key, plain):if len(key)!=32:return "error!"cipher_txt = b""cipher_arr = []cipher = AES.new(key, AES.MODE_ECB, "")plain = [plain[i:i+32] for i in range(0, len(plain), 32)]print plaincipher_arr.append(cipher.encrypt(plain[0]))cipher_txt += cipher_arr[0]for i in range(1, len(plain)):cipher = AES.new(cipher_arr[i-1], AES.MODE_ECB, "")cipher_arr.append(cipher.encrypt(plain[i]))cipher_txt += cipher_arr[i]return cipher_txtkey = random.getrandbits(256)
key = long_to_bytes(key)s = ""
with open("flag.txt","r") as f:s = f.read()f.close()with open("flag_cipher","wb") as f:f.write(MyOwnCBC(key, s))f.close()
简单的对MyOwnCBC.py脚本进行分析,可以发现,其实就是ECB模式下的AES,然后将每个分组单独进行了AES ECB加密,可以看到的是每一组AES加密的key为上一组加密结果的密文。
出题人设计这个题目的意图应该是想带大家了解一下AES CBC模式,用ECB模式进行一个大概的模拟(当然不是这个原理)。主要是想表达CBC模式下会把上一轮的加密影响扩散到下一轮的意思吧。
那解密也很简单,因为key其实就是每组加密后的密文嘛,直接AES ECB模式下解密即可。
脚本如下
from Crypto.Cipher import AES
f=open("flag_cipher","rb")
#<_io.BufferedReader name='flag_cipher'>
st=f.read()
#b'\xe5\xdf\x94sJ\xc2\xcd\x04\xeb\xb7\xcf\x05(\xbe\x98\\\xe9\xc3^\x1f!\xfb\xea6\xdac\x1f\xfe\x901\xbb\x13[+\xb5|\xb3_\x06\x08\xa71JL\xe4\xf2\x05\x88\x1d\xe1c\xd99\xf6\xb9\'>c\xbbi\x84\x80l\x18st\xdf\tY\x91\xf5kb\xf55\xefd[hC\x844\tx\x95\xdc\x14\xbb@\xb5u\x12\xfc\nHC)\xccv\xe8\x86\xe1\xc2\xd7\xd6\xb5\xc3\xf4(g\xd6\x99\x8e\x95*M\xaf^\xde\x07=\x16\xc5G\xe7\xfa\xd4\xfcn8\xd66\xe2\x1e\xa7\xb1\xf5{\xdb\x90?\x97`z\x02S\'/\xfdH\xd6\xc2M\xc7\xf6\xdb\x0cu=|\xe7\x85\x10\x18\xa9k\xa9\x05-R\x8e\x8bS\xd8\x07\xc7\xf3N,a\xcd\x98AD\x91\x0e\x08\xc2\xb60\xbe ~@\xd3/S\xe8\x8878&\x001C\x8c\x05B\x0b\xad\x9b\\\x19\x85|\x02X\x0e\x9f\xb43;\xabw\x8c\xb2a\xdc\x88\x9e\xac\x17\xf82\xbb\x9f\xb0z\xbc\x13\xab[X\xe1\x8a\xf9\xed\xd8\x9e\xf4:\x08\xd3:\x0cH\x9a\xdal\x0c\xfb\xb9\xd0\x01\xe4m\x06\xf9e\xae\xfc\xbe\x1d\x18\x89+Y\x00\t\xf8\x17\xb6\xe88\xc4\xb6w\xba\x06\x9a\x93\x13\xbf\xb2\x1a\xf7c\x03\x02\xd2}\xb1\xc7\x9f\xe4\x01\xa6\x0c\x87\x7f\xaf\n\xbcb\xd9\xa6\xb2\x06\xc8u\xc4\xf39k)k\xf72\xeb\xc5\x06\x91\x86~\x9ftWK\xaa\xe31\xa7\x93\xc4J\xd1\xf9\x12\x15C>E~\x8bo\xc7\xc8\xcd\x8d\xe9l\xe5\n\xd6\xc7\xe1\x8b\x98f\x9d\xbc\xae\xd6\xcf\xdc\x1a\xad\xd1\xd0\x0f\x94\xa2D\x92\xc1\xae\xc6/\xe4\xcb\xd1\xc7\xcaG4-\x8a=\xd5O\x8f\xc8\xa4\x80x\x0e\x94o\xae\xf1\xeb\xa2N8UY\x1e\x96\xf2_\xc9\x95I)\x1d^\xfaN\x95\x9a\x89\xfdk8T)\xd7v\xbe\x84\x88\x87\xb3\xea<D0\xd1\x81\x11n&U\xbb\x9aO\xf0\xecY\x15\xf1m\xe2\xa8\x7f\xf7\xe9\x9f\xa1\xd9\xa0\xe8gH\x8b\xaf\xb9r\x8a\xdf2\xbe\x87\xbc\xab\xa6YYw\xa4j^\x10U_\x1e\xc7\x7f\xb6W\xa4\xc6\xa4\x1fd\xa2\xee\xfc\xe6\xa7\x1e\xd3\xc9\x12_\x1d\xcd\xe2\x98\x9eg\xb0\x0b\x83o\xaa\x07\xd7jJ\x0e\x96\'\xed\x00jI}[dRp9\x82h\xc6\xf2g\xcec\x1e\x95\x03\xc6\xeb/\r8\x02\xcb0K\x1c\x8e\xf7>@\x19\xa03\x9e;@\x9f\xd4\xfb\x8e\xb4\xcchT\xf94Ds*\xbbX2\xf1:\xdb\xf7\xe3\x85y\xa7\xcfm\x89\xbf_Y\x9eGo\xa2c\x80\x9c0MI\\Z\xa8\xa4#\xb3k[\x99\x99h-\x99\xf7\xae\xd4\xeb\xc6g\xa8;4M:3\xd2\x80\x85\r\r\xd9\x82\xa0\xc6\xae\x8c\x13edZ\xacRG\xd3;\x95t3\x9e\xe6\xdf\x85\xe8\xab2b\xb3@\x1f\td\xfe\xd1c\xe2?\xb3\xdc\x85&\x82\x14\x97\x84\t\x00\xde\x12\x1a\xb1\xf3\x8e\xe6N~\xff\x7fi^\n`P\x0e\'\xd4\xa3\x16\x11vp\xcb\xc5\x0f\x94\xc0\xf7H\xf1\x97\xf3\xae\x02\xde\xaf?\xee"\xb2yIq\xa6M\xf3F\xfa<{\\\xfdd\xbf\x90\tV\x9b\xe7+\xc4\x14\x11\xe8\xff.\xdf\xed\xce\x14\xb8\x87DJ\x18\x00\x90\x95\xc1WP\xd4\x18\x1b\x9d\xfc\xa2\xfe\xa1$5\x17\xa0\x98\xe0m_u\xc0\xe5\xef\x88\xbd\x82Q\x81-\xe7\x99\x07\x90Ej\x8d\x93j\xa6\x8f\xc6\xd2\xeen\xc5`\xb9\xc1\x91rI\x16\xcd\xef\xb3\x00\xc2\x96F\x8b#T\xc7E\xeb\x1e\x99%AF\xc9\x90>\xcd\x01\x861A\x9b5\x18\xa7Z\x93\x0b5\xb0E\x83=\xb2\x14\x0b\xa2\x99\xe2\xbd\xb2A\xd1YR\xa9y\xdf\xebq\xa0\xb6\x05rO\x08\x97\xcdsr\x9a\xfd\x04\xb1\x94\xf2\x1as\xfc\x0e\xaa\xdb\xce\x9580lC\xa8\x97_\x93\xb0\xe7\x91;W\xa8v\xbe\xa75\\\x06Y\x05\x17\x8f\xdbih\x89\xdaa\x9e\xb6}\xc4\x89\'/\x94\xdc\x07\xa7\x9b\xa5\x87\xd8*\t\x84\xcev6\x86\xb3\x8a\x1b\xfa\xebu\xa4\x06\x93:\xbfbh\x17\xe7\x1c[\xe6\x88\xa3\x82\xb6\xc5\xf5\x1d\x85M\x10k\x10f\x11\x17\xfba\xa2\x11\xf7\xda\xd7Fs0\x9d\x1bF\xfc\x878\xdd\x12>"Ou\x93\xaee\xd3w\xdbJ\xeaM\xe2\xc4\xaa\xeb\x01\xb0<\xfe\xbe\x16\xfe\xd9 9\x04+\x04Bg\xd6Y\x9b\xe2rI\xb0&S\x9a\x1c\xa2\xf5`\x84s\x90\xd1\x85a\xde\xf3\xc8r\xacY[Y}\xbd\x9a\xef\xb9\x82\x8bK?\xec\xf7\xcdI\xa0\x04SK\x0b\x95\xc9\xa4\xe26\x0f@\xa3j\x0c8\xc6Q\xf8\xcb]\xa3W\xf9#7UQ\x11\x9f\xc5t\x07m\x8a6O^\x88g\xf39f\xd8\xd9\x9c\x18[\xe3\x1dn\xfe9\xdd\xe1:\x9b\xc9t\x9d\x87\x04\xc5\x93T\xb3\x1e\xbb@wC\rS\xe3\xb7|\xd1>\\\xb3H\xb7R\xce) \x0eR\x8c\x8e\xa6k\xe0\xc7 W\xaa\xe9\xf2\xea\x0fK\xc5\xb5\xb3\x08\\\xd6"b\xb6{\x9a\x16\x1aIO\x1a\xf0\xfd\xde/(\xb3\x8bB!Hk\x8e\xe6\x10\x18@\xd2y6\xf9u\xdfX\xebO;k\x90V.]b]u\x1c\xd1\x91\x15\xab\x1a!H\xf7>\x81pS\xcb\x11 a\xdah\x93\xe8\xb6b\x0b\xbc%e\xa1\x9e\xd8\x81\x98\t\xb2\xcc\x133:\x99\xf1TY\x9cl\tB\x8aXz\xb9k\xa68e\xc3p\x00\xd5j|\x93Yz\xcd\x17"JT\xb6(b"t\xe7p6\x03\xaf\xcc\xf9n\xdb%\xee@:\xa9\xea\x0cV\xb8\x93\xe5\xf8\xc9\x17\x1f\x91\x8d\xadF\x10\xdb4\xb2\xc0\x7f\xe2\xad\xbfwZ\xa1\xc4\xa7\xf1\x93\x0e\xe0\xed\xcc\xe5K|Kd"\xd4\x00\xbf8\x7ff9\xb2\xecm\xeb\xa5X\x03HO\xc2\x97\x01\x86\xff\xd1\xc1\xa5E\xd4Z\xd7\xe4#H\xd4\x02c\x8e\xe2\x94\x93s\xbb\xee;<gT\\\xc4\xea\x92\xc5\xd4)\xf3\xd9v"G\x98\xd7gx"]\xac\xec\xe3\xef\xecy\xb1\xbav\x9c\xd4\x1d\xee\x91\xd5\x90\xb1\xeb\xd3$\xe5\x96\x91w[eO\xf4liB\nM\x96\x9b\x92\xc9\x03\xafs\xd8\x83\xd6!\xa1\x90/\xcba\xdf\xbb\xa6\x15\\\xa3t\xd8\xb3j\xb2\xd3\xd5\x19\xf6\xa0\x16\xefE\xca\xbc\xbaB\xf3#\xa0\x0c\xec\x04wp\x15\x06~\x0c\x9c\x17\x8b\xa6\x04qr\xe0\x1f\xf49\x84YD\xd7\xcf\\1v \xe5$\xcc\xf9d\xdb\xb2\x12e\x0f8\x08\xf5\xa8\x8d\xd3\xc74H\xfd\xec\xc8\xa4\xc1\x9b\xa0R\xf4\x130\xc3\xe4\xe7\xc5\xe9\\fU\t\x0fgK\xe7\xfd]\n\x17\x1de\x95\xcd9%\xd6}&c\x0e\xa10\xdcy.O\x8b\xc6\x91\xe5\x88]T?$\x14~\x97\xcf\x13\xb0\xcc\x88\xdbN\xd3\x13\xe9\xcd\x9c\xe2\x80\x03%\xcf;\xfdm\x91;\xc2\xc1\xb1T\xe5\xb7\xb1k5\x9a\x1c\x90\xc0\x92\xf5\x88U\xaaQ\xa03gs\x0fX"U:\xf6C<\xe0\xedS\xdfE\xcb\xf3\x06\x03\x83\xcf8\x0c\x85\x03\xfc\xad-Ku=\xa8\xd6lY\x91su%\n(\x15\xaa\xba)\'=1+\x18F\x88\x94c\x9e'print(len(st))
#1696
def MyOwnCBC(key, plain):cipher_txt = b""cipher = AES.new(key, AES.MODE_ECB)cipher_txt=cipher.decrypt(plain)
#b'_be_fooled_by_yourself}~~~~~~~~~'
#b"s.\n\nAh you found it~ afctf{Don't"
#b'as authenticated encryption mode'
#b'an efficient way, and are known '
#b'identiality and authenticity in '
#b' modes of operation combine conf'
#b' cryptographic goal. Some modern'
#b'otection as an entirely separate'
#b'evelopment regarded integrity pr'return cipher_txt
#for i in range(len(st)//32):
flag=""
for i in range(1,10):plain=MyOwnCBC(st[(52-i-1)*32:(52-i)*32],st[(52-i)*32:(53-i)*32])flag=plain.decode()+flag
print(flag)
其实我个人的话就写到cipher_txt就行但是嘛为了美观嘛,运行得到
evelopment regarded integrity protection as an entirely separate cryptographic goal. Some modern modes of operation combine confidentiality and authenticity in an efficient way, and are known as authenticated encryption modes.Ah you found it~ afctf{Don't_be_fooled_by_yourself}~~~~~~~~~
138.LeftOrRight
查看题目jpg文件,用010打开可以发现开头和结尾有十六进制,我们在线转文本得到
f09e54c1bad2x38mvyg7wzlsuhkijnop
905e4c1fax328mdyvg7wbsuhklijznop
题目提示Left?Middle?No,I want right!(flag is right?!)
字母相同…顺序不同,再分析一下题目,left,mid都不要,只要right,然后这个地方又是一个树,二叉树1
前序遍历,中序遍历,后序遍历,
前尝试把文件尾部的字符串交上去,不对.
那就是第一个是前序遍历,第二个是中序,求后序遍历:
def get_after_deep(pre, mid, a):#已知前中,求后,a就是后序if len(pre) == 1:a.append(pre[0])returnif len(pre) == 0:returnroot = pre[0]root_index = mid.index(root)get_after_deep(pre[1:root_index+1], mid[:root_index], a)get_after_deep(pre[root_index+1:], mid[root_index+1:], a)a.append(root)return adef get_hou():pre=input("请依次输入前序遍历、中序遍历的结果,以换行分割:\n")mid=input()pre_list=list(pre)mid_list=list(mid)a=[]res_list=get_after_deep(pre,mid,a)res="".join(res_list)print("后序遍历为:",res)
get_hou()
运行得到951c4e03xm82yw7gvdakhusjilponzbf
139.[watevrCTF 2019]ECC-RSA
查看题目
from fastecdsa.curve import P521 as Curve
from fastecdsa.point import Point
from Crypto.Util.number import bytes_to_long, isPrime
from os import urandom
from random import getrandbitsdef gen_rsa_primes(G):urand = bytes_to_long(urandom(521//8))while True:s = getrandbits(521) ^ urandQ = s*Gif isPrime(Q.x) and isPrime(Q.y):print("ECC Private key:", hex(s))print("RSA primes:", hex(Q.x), hex(Q.y))print("Modulo:", hex(Q.x * Q.y))return (Q.x, Q.y)flag = int.from_bytes(input(), byteorder="big")ecc_p = Curve.p
a = Curve.a
b = Curve.bGx = Curve.gx
Gy = Curve.gy
G = Point(Gx, Gy, curve=Curve)e = 0x10001
p, q = gen_rsa_primes(G)
n = p*qfile_out = open("downloads/ecc-rsa.txt", "w")file_out.write("ECC Curve Prime: " + hex(ecc_p) + "\n")
file_out.write("Curve a: " + hex(a) + "\n")
file_out.write("Curve b: " + hex(b) + "\n")
file_out.write("Gx: " + hex(Gx) + "\n")
file_out.write("Gy: " + hex(Gy) + "\n")file_out.write("e: " + hex(e) + "\n")
file_out.write("p * q: " + hex(n) + "\n")c = pow(flag, e, n)
file_out.write("ciphertext: " + hex(c) + "\n")
ECC Curve Prime: 0x1ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff
Curve a: -0x3
Curve b: 0x51953eb9618e1c9a1f929a21a0b68540eea2da725b99b315f3b8b489918ef109e156193951ec7e937b1652c0bd3bb1bf073573df883d2c34f1ef451fd46b503f00
Gx: 0xc6858e06b70404e9cd9e3ecb662395b4429c648139053fb521f828af606b4d3dbaa14b5e77efe75928fe1dc127a2ffa8de3348b3c1856a429bf97e7e31c2e5bd66
Gy: 0x11839296a789a3bc0045c8a5fb42c7d1bd998f54449579b446817afbd17273e662c97ee72995ef42640c550b9013fad0761353c7086a272c24088be94769fd16650
e: 0x10001
p * q: 0x118aaa1add80bdd0a1788b375e6b04426c50bb3f9cae0b173b382e3723fc858ce7932fb499cd92f5f675d4a2b05d2c575fc685f6cf08a490d6c6a8a6741e8be4572adfcba233da791ccc0aee033677b72788d57004a776909f6d699a0164af514728431b5aed704b289719f09d591f5c1f9d2ed36a58448a9d57567bd232702e9b28f
ciphertext: 0x3862c872480bdd067c0c68cfee4527a063166620c97cca4c99baff6eb0cf5d42421b8f8d8300df5f8c7663adb5d21b47c8cb4ca5aab892006d7d44a1c5b5f5242d88c6e325064adf9b969c7dfc52a034495fe67b5424e1678ca4332d59225855b7a9cb42db2b1db95a90ab6834395397e305078c5baff78c4b7252d7966365afed9e通过分析代码,我们可以知道
这个题是 ECC 和 RSA 的混合加密,尽管用了两种加密方式,但加密并不复杂。
我们只需要求出 ,p,q的值就能得到 flag 了。点(p,q)是椭圆曲线上的两个点。代入椭圆曲线的方程就能解出 p,q了。
q ^ 2 = p ^ 3 + a * p + b
又因为 n = p * q ,将方程左右两边同时乘以 p ^ 2
所以有:n ^ 2 = p ^ 5 + a * p ^ 3 + b * p ^2
ECC加密学习
用sage计算p
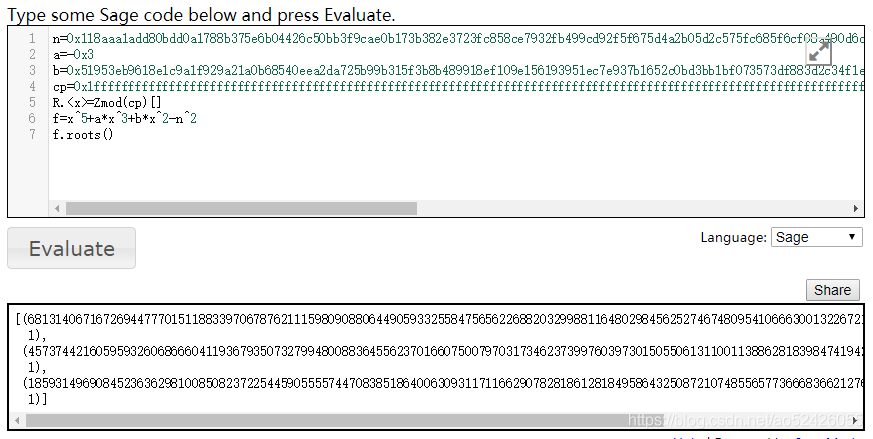
得到
[(6813140671672694477701511883397067876211159809088064490593325584756562268820329988116480298456252746748095410666300132267213094431909630229631434972416225885,1),(4573744216059593260686660411936793507327994800883645562370166075007970317346237399760397301505506131100113886281839847419425482918932436139080837246914736557,1),(1859314969084523636298100850823722544590555574470838518640063093117116629078281861281849586432508721074855657736668366212762253040197962779753163192386773060,1)]
我是一个一个试的,第二个符合条件
n=0x118aaa1add80bdd0a1788b375e6b04426c50bb3f9cae0b173b382e3723fc858ce7932fb499cd92f5f675d4a2b05d2c575fc685f6cf08a490d6c6a8a6741e8be4572adfcba233da791ccc0aee033677b72788d57004a776909f6d699a0164af514728431b5aed704b289719f09d591f5c1f9d2ed36a58448a9d57567bd232702e9b28f
p=4573744216059593260686660411936793507327994800883645562370166075007970317346237399760397301505506131100113886281839847419425482918932436139080837246914736557
import gmpy2
q=n//p
ciphertext=0x3862c872480bdd067c0c68cfee4527a063166620c97cca4c99baff6eb0cf5d42421b8f8d8300df5f8c7663adb5d21b47c8cb4ca5aab892006d7d44a1c5b5f5242d88c6e325064adf9b969c7dfc52a034495fe67b5424e1678ca4332d59225855b7a9cb42db2b1db95a90ab6834395397e305078c5baff78c4b7252d7966365afed9e
e=0x10001
d=gmpy2.invert(e,(p-1)*(q-1))
import Crypto.Util.number
print(Crypto.Util.number.long_to_bytes(gmpy2.powmod(ciphertext,d,n)))#b'watevr{factoring_polynomials_over_finite_fields_is_too_ez}'140.[V&N2020 公开赛]Backtrace
查看题目
# !/usr/bin/env/python3
import randomflag = "flag{" + ''.join(str(random.getrandbits(32)) for _ in range(4)) + "}"with open('output.txt', 'w') as f:for i in range(1000):f.write(str(random.getrandbits(32)) + "\n")print(flag)
和一个数字文件
2.分析
MT19937随机数破解的破解,恕我这个数学白痴理解不能啊。。。
这里只能简单的说一下我理解的“结论”。
(1)MT19937算法生产随机数的过程
1.利用seed初始化624的状态
2.对状态进行旋转
3.根据状态提取伪随机数
(2)逆向 extract_number
extract_number函数,可以发现输出的伪随机数是对state[i]进行了异或,位运算后的结果。预测随机数的题型就是基于对extract_number 函数的逆向,我们可以根据题目输出的随机数逆向extract_number得到对应的n个state(n>624),实际上只需要前624个随机数恢复前624个state,就可以预测此后生成的随机数。
(3)逆向twist
在已知连续624个随机数时(state没有进行twist),可以还原state,预测后续的随机数。那么如何获得624个随机数之前的随机数呢?此时可以考虑,逆向twist获得前一组的state,进而获得前一组的624个随机数。
此题就是一个逆向twist。
3.解题思路
题目要求恢复前四个随机数(就是flag)。
这里要提一点的是不要纠结那个‘_’,其实跟Ii没有区别。就是连续取4个随机数的意思。
前面说过。逆向twist我们需要连续的624个随机数才能获得上一组随机数的状态,这里只有1000个随机数,这里的前4位随机数丢失,而前4位随机数产生的新状态对应第624,625,626,627位随机数的状态,而他们的状态是可逆的。所以不需要完整的连续624个随机数,也可以求解完整的state。
说实话还是不大理解,但是大概可以知道就是我们可以用后面产生的1000个随机数,利用随机数状态可逆的问题,反向(backtrace)得到之前产生的随机数。
直接抄袭了大神的脚本:
#!python3
# -*- coding: utf-8 -*-
# @Time : 2020/10/25 21:59
# @Author : A.James
# @FileName: exp2.py
from random import Random# right shift inverse
def inverse_right(res,shift,bits=32):tmp = resfor i in range(bits//shift):tmp = res ^ tmp >> shiftreturn tmp# right shift with mask inverse
def inverse_right_values(res,shift,mask,bits=32):tmp = resfor i in range(bits//shift):tmp = res ^ tmp>>shift & maskreturn tmp# left shift inverse
def inverse_left(res,shift,bits=32):tmp = resfor i in range(bits//shift):tmp = res ^ tmp << shiftreturn tmp# left shift with mask inverse
def inverse_left_values(res,shift,mask,bits=32):tmp = resfor i in range(bits//shift):tmp = res ^ tmp << shift & maskreturn tmpdef backtrace(cur):high = 0x80000000low = 0x7fffffffmask = 0x9908b0dfstate = curfor i in range(3,-1,-1):tmp = state[i+624]^state[i+397]# recover Y,tmp = Yif tmp & high == high:tmp ^= masktmp <<= 1tmp |= 1else:tmp <<=1# recover highest bitres = tmp&high# recover other 31 bits,when i =0,it just use the method again it so beautiful!!!!tmp = state[i-1+624]^state[i+396]# recover Y,tmp = Yif tmp & high == high:tmp ^= masktmp <<= 1tmp |= 1else:tmp <<=1res |= (tmp)&lowstate[i] = resreturn statedef recover_state(out):state = []for i in out:i = inverse_right(i,18)i = inverse_left_values(i,15,0xefc60000)i = inverse_left_values(i,7,0x9d2c5680)i = inverse_right(i,11)state.append(i)return statef = open("output.txt","r").readlines()
c = []
for i in range(1000):c.append(int(f[i].strip()))partS = recover_state(c)
state = backtrace([0]*4+partS)[:624]
# print(state)
prng = Random()
prng.setstate((3,tuple(state+[0]),None))
flag = "flag{" + ''.join(str(prng.getrandbits(32)) for _ in range(4)) + "}"
print(flag)
#flag{1886737465387686573924175753923879771350}
这道题没看懂 大佬脚本也一样这题引用wp
141.[GUET-CTF2019]Uncle Sam
查看题目
from Crypto.Util.number import *def generkey(k):p, q = getPrime(k), getPrime(k)pubkey = p**2 * qn = pubkeyl = (p-1)*(q-1) / gcd(p-1, q-1)privkey = inverse(n, l)return pubkey, privkey
def encrypt(m, pubkey):return pow(bytes_to_long(m), pubkey, pubkey)# pubkey = 2188967977749378274223515689363599801320698247938997135947965550196681836543275429767581633044354412195352229175764784503562989045268075431206876726265968368605210824232207290410773979606662689866265612797103853982014198455433380266671856355564273196151136025319624636805659505233975208570409914054916955097594873702395812044506205943671404203774360656553350987491558491176962018842708476009578127303566834534914605109859995649555122751891647040448980718882755855420324482466559223748065037520788159654436293431470164057490350841209872489538460060216015196875136927502162027562546316560342464968237957692873588796640619530455268367136243313422579857823529592167101260779382665832380054690727358197646512896661216090677033395209196007249594394515130315041760988292009930675192749010228592156047159029095406021812884258810889225617544404799863903982758961208187042972047819358256866346758337277473016068375206319837317222523597
# privkey = 1430375790065574721602196196929651174572674429040725535698217207301881161695296519567051246290199551982286327831985649037584885137134580625982555634409225551121712376849579015320947279716204424716566222721338735256648873164510429206991141648646869378141312253135997851908862030990576004173514556541317395106924370019574216894560447817319669690140544728277302043783163888037836675290468320723215759693903569878293475447370766682477726453262771004872749335257953507469109966448126634101604029506006038527612917418016783711729800719387298398848370079742790126047329182349899824258355003200173612567191747851669220766603
# enc = 1491421391364871767357931639710394622399451019824572362288458431186299231664459957755422474433520889084351841298056066100216440853409346006657723086501921816381226292526490195810903459483318275931326433052468863850690793659405367902593999395060606972100169925074005992478583035226026829214443008941631771292291305226470216430735050944285543542354459162474346521327649934512511202470099020668235115245819634762067338432916012664452035696422865651002305445711778476072004708256200872226475346448360491248823843688268126341094612981308791499434770936360676087490303951728563482686307164877000300082742316368597958297217061375140696272398140310043942637287763946305961019518639745426370821124559939597559475362769382796386720030343305889701616194279058139516811941262747298761646317383112470923295543635754747288259324745583689440061956478083777663996487389553238481759103908588004219390662578446313004404784835263543083088327198上脚本
from Crypto.Util.number import *
'''
def generkey(k):p, q = getPrime(k), getPrime(k)pubkey = p**2 * qn = pubkeyl = (p-1)*(q-1) / gcd(p-1, q-1)privkey = inverse(n, l)return pubkey, privkey
def encrypt(m, pubkey):return pow(bytes_to_long(m), pubkey, pubkey)# pubkey = 2188967977749378274223515689363599801320698247938997135947965550196681836543275429767581633044354412195352229175764784503562989045268075431206876726265968368605210824232207290410773979606662689866265612797103853982014198455433380266671856355564273196151136025319624636805659505233975208570409914054916955097594873702395812044506205943671404203774360656553350987491558491176962018842708476009578127303566834534914605109859995649555122751891647040448980718882755855420324482466559223748065037520788159654436293431470164057490350841209872489538460060216015196875136927502162027562546316560342464968237957692873588796640619530455268367136243313422579857823529592167101260779382665832380054690727358197646512896661216090677033395209196007249594394515130315041760988292009930675192749010228592156047159029095406021812884258810889225617544404799863903982758961208187042972047819358256866346758337277473016068375206319837317222523597
# privkey = 1430375790065574721602196196929651174572674429040725535698217207301881161695296519567051246290199551982286327831985649037584885137134580625982555634409225551121712376849579015320947279716204424716566222721338735256648873164510429206991141648646869378141312253135997851908862030990576004173514556541317395106924370019574216894560447817319669690140544728277302043783163888037836675290468320723215759693903569878293475447370766682477726453262771004872749335257953507469109966448126634101604029506006038527612917418016783711729800719387298398848370079742790126047329182349899824258355003200173612567191747851669220766603
# enc = 1491421391364871767357931639710394622399451019824572362288458431186299231664459957755422474433520889084351841298056066100216440853409346006657723086501921816381226292526490195810903459483318275931326433052468863850690793659405367902593999395060606972100169925074005992478583035226026829214443008941631771292291305226470216430735050944285543542354459162474346521327649934512511202470099020668235115245819634762067338432916012664452035696422865651002305445711778476072004708256200872226475346448360491248823843688268126341094612981308791499434770936360676087490303951728563482686307164877000300082742316368597958297217061375140696272398140310043942637287763946305961019518639745426370821124559939597559475362769382796386720030343305889701616194279058139516811941262747298761646317383112470923295543635754747288259324745583689440061956478083777663996487389553238481759103908588004219390662578446313004404784835263543083088327198
'''
def gcd(a, b):if a < b:a, b = b, awhile b != 0:temp = a % ba = bb = tempreturn adef generkey(k):p, q = getPrime(k), getPrime(k)pubkey = p ** 2 * qn = pubkeyl = (p - 1) * (q - 1) / gcd(p - 1, q - 1)privkey = inverse(n, l)return pubkey, privkeydef encrypt(m, pubkey):return pow(bytes_to_long(m), pubkey, pubkey)pubkey = 2188967977749378274223515689363599801320698247938997135947965550196681836543275429767581633044354412195352229175764784503562989045268075431206876726265968368605210824232207290410773979606662689866265612797103853982014198455433380266671856355564273196151136025319624636805659505233975208570409914054916955097594873702395812044506205943671404203774360656553350987491558491176962018842708476009578127303566834534914605109859995649555122751891647040448980718882755855420324482466559223748065037520788159654436293431470164057490350841209872489538460060216015196875136927502162027562546316560342464968237957692873588796640619530455268367136243313422579857823529592167101260779382665832380054690727358197646512896661216090677033395209196007249594394515130315041760988292009930675192749010228592156047159029095406021812884258810889225617544404799863903982758961208187042972047819358256866346758337277473016068375206319837317222523597
privkey = 1430375790065574721602196196929651174572674429040725535698217207301881161695296519567051246290199551982286327831985649037584885137134580625982555634409225551121712376849579015320947279716204424716566222721338735256648873164510429206991141648646869378141312253135997851908862030990576004173514556541317395106924370019574216894560447817319669690140544728277302043783163888037836675290468320723215759693903569878293475447370766682477726453262771004872749335257953507469109966448126634101604029506006038527612917418016783711729800719387298398848370079742790126047329182349899824258355003200173612567191747851669220766603
enc = 1491421391364871767357931639710394622399451019824572362288458431186299231664459957755422474433520889084351841298056066100216440853409346006657723086501921816381226292526490195810903459483318275931326433052468863850690793659405367902593999395060606972100169925074005992478583035226026829214443008941631771292291305226470216430735050944285543542354459162474346521327649934512511202470099020668235115245819634762067338432916012664452035696422865651002305445711778476072004708256200872226475346448360491248823843688268126341094612981308791499434770936360676087490303951728563482686307164877000300082742316368597958297217061375140696272398140310043942637287763946305961019518639745426370821124559939597559475362769382796386720030343305889701616194279058139516811941262747298761646317383112470923295543635754747288259324745583689440061956478083777663996487389553238481759103908588004219390662578446313004404784835263543083088327198n = pubkey
d = privkeypow2 = pow(2, n * d, n)
assert pow2 != 2g = gcd(pow2 - 2, n)
assert g != 1 and g != n
assert n % g == 0pq = g
m=pow(enc, d, pq)
flag=long_to_bytes(m)
print(flag)
运行得到flag{61e19444-7afb-11e9-b704-4ccc6adfc6f0}
142.[b01lers2020]safety_in_numbers
查看题目
pubke.pem储存了n和e。
flag.enc是加密结果
enc.py是加密脚本
用脚本读pubke.pem里面的ne,n太大了,写不进来就截个图
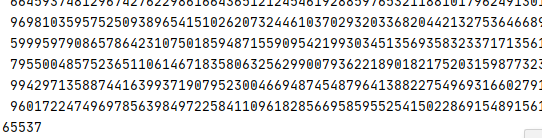
n很大,e很小。那么m就是c直接开e次方即可。
import gmpy2e = 65537
with open('flag.enc','rb') as f:cipher = f.read()
c = int.from_bytes(cipher, byteorder='little')
m = gmpy2.iroot(c,e)[0]
print(m)
print(hex(m))#转换十六进制
print(bytes.fromhex(hex(m)[2:])[::-1])#ascll码
运行得到pctf{!fUtuR3_pR00f}
143.[AFCTF2018]一道有趣的题目
#加密代码
def encrypt(plainText):space = 10cipherText = ""for i in range(len(plainText)):if i + space < len(plainText) - 1:cipherText += chr(ord(plainText[i]) ^ ord(plainText[i + space]))else:cipherText += chr(ord(plainText[i]) ^ ord(plainText[space]))if ord(plainText[i]) % 2 == 0:space += 1else:space -= 1return cipherText
首先要处理space部分,space每一次变化都和每个明文字符的最后一位有关,明文的长度和密文的长度是一样的,因此可以先求出密文的长度,发现是28,于是尝试爆破每个明文字符的最后一位.有228种可能.
处理完space部分后,发现每一次加密都是一个方程,一共有28个方程,也一共有28个未知数,但是前几个未知数我们可以猜测一下为 ‘a’ ‘f’ ‘c’ ‘t’ ‘f’ ‘{’
这样我们很快就可以将所有的未知数给求解出来了.
def crackit():'''暴力求出每个明文字符的最后一位:return: 每个明文字符最后一位组成的字符串'''tag=b'\x15\x12\r\x1a\n\x08\x10\x01\n\x03\x1d>1\x00\r\x1d\x17\r\x17;\r\x17;\x0c\x07\x06\x02\x06'for x in range(268435456):temp=bin(x)[2:].zfill(28)space = 10flag=0for i in range(len(temp)):if i + space < len(temp) - 1:tempx= int(temp[i]) ^ int(temp[i + space])else:tempx= int(temp[i]) ^ int(temp[space])if tempx!=(tag[i]%2):flag=1breakelif int(temp[i]) % 2 == 0:space += 1else:space -= 1if flag!=1:print(temp)#temp ='1010011010010101111111101001'def crackit_2():'''解出每个方程中的明文字符的序号.:return: 每个方程中的明文字符的序号组成的列表.'''tag=b'\x15\x12\r\x1a\n\x08\x10\x01\n\x03\x1d>1\x00\r\x1d\x17\r\x17;\r\x17;\x0c\x07\x06\x02\x06'temp ='1010011010010101111111101001'space = 10g=[]for i in range(len(temp)):if i + space < len(temp) - 1:tempx = int(temp[i]) ^ int(temp[i + space])g.append((i,i+space))else:tempx = int(temp[i]) ^ int(temp[space])g.append((i,space))if int(temp[i]) % 2 == 0:space += 1else:space -= 1return g
def solve(g,m):'''解明文方程组:param g: 明文方程组:param m :密文:return: 明文'''plain=[ord('a'),ord('f'),ord('c'),ord('t'),ord('f'),ord('{')]+[-1]*22#明文未知数while -1 in plain:for i in range(28):if plain[i] != -1:for j in range(len(g)):if g[j][0] == i or g[j][1] == i:if g[j][0] == i:plain[g[j][1]] = m[j] ^ plain[i]if g[j][1] == i:plain[g[j][0]] = m[j] ^ plain[i]return plain#[97, 102, 99, 116, 102, 123, 99, 114, 121, 112, 116, 97, 110, 97, 108, 121, 115, 105, 115, 95, 105, 115, 95, 104, 97, 114, 100, 125]tag=b'\x15\x12\r\x1a\n\x08\x10\x01\n\x03\x1d>1\x00\r\x1d\x17\r\x17;\r\x17;\x0c\x07\x06\x02\x06'#密文
g=crackit_2()
print(g)
plain=solve(g,tag)
print(plain)
flag=''
for i in plain:flag+=chr(i)
print(flag)#afctf{cryptanalysis_is_hard}144.[NCTF2019]Reverse
查看题目
import os
import pyDesflag = "NCTF{******************************************}"
key = os.urandom(8)d = pyDes.des(key)
cipher = d.encrypt(flag.encode())with open('cipher', 'wb') as f:f.write(cipher)# Leak: d.Kn[10] == [0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 1]知道一个子密钥,尝试爆破所有可能的子密钥的情况,一共有28 种.
需要注意的细节:
** 每轮循环左移的位数不一定相同**
** d.Kn[10] 已知,说明已经进行了11轮了(每一轮生成一个子密钥),因此要做sum(movnum[:11])次逆运算**
这题我也是看了大佬的wp
import copy
import pyDes
key='********'
d=pyDes.des(key)
key10=[0, 1, 0, 0, 0, 1, 0, 1, 0, 1, 1, 0, 1, 1, 0, 1, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 1, 0, 0, 0, 0, 1, 0, 0, 1, 0, 0, 0, 1, 0, 0, 0, 0, 1]
PC1=[56, 48, 40, 32, 24, 16, 8, 0, 57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 60, 52, 44, 36, 28, 20, 12, 4, 27, 19, 11, 3]
PC2=[13, 16, 10, 23, 0, 4, 2, 27, 14, 5, 20, 9, 22, 18, 11, 3, 25, 7, 15, 6, 26, 19, 12, 1, 40, 51, 30, 36, 46, 54, 29, 39, 50, 44, 32, 47, 43, 48, 38, 55, 33, 52, 45, 41, 49, 35, 28, 31]
movnum = [1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1]#对应16轮中每一轮的循环左移位数
def gen_key(C1,D1,k):tempc=C1tempd=D1for i in range(k):tempc = tempc[1:] + tempc[:1]tempd = tempd[1:] + tempd[:1]tempCD1=tempc+tempdtempkey=[]for i in range(len(PC2)):tempkey.append(tempCD1[PC2[i]])return (tempkey,tempCD1)#轮运算得到下一轮子密钥
def re_gen_key(C1,D1):tempc=C1[-1:]+C1[:-1]tempd=D1[-1:]+D1[:-1]tempCD1=tempc+tempdreturn tempCD1 #轮运算得到上一轮CD
def get_key(CD):tempkey=[]for i in range(len(PC2)):tempkey.append(CD[PC2[i]])return tempkey
def RE_pc2():CD1=['*']*56for i in range(len(PC2)):CD1[PC2[i]]=key10[i]#初步还原CD1results=[]for i in range(256):temp=bin(i)[2:].zfill(8)tempi=copy.deepcopy(CD1)d=0for j in range(len(tempi)):if tempi[j]=='*':tempi[j]=eval(temp[d])d=d+1results.append(tempi)return results
f=open('cipher','rb')
flag_enc=f.read()
results=RE_pc2()
for i in range(len(results)):temp=results[i]for j in range(sum(movnum[:11])):temp=re_gen_key(temp[:28],temp[28:])tempK=[]Z=tempfor j in range(16):tempx=gen_key(Z[:28],Z[28:],movnum[j])tempK.append(tempx[0])Z=tempx[1]d.Kn=tempKprint(d.decrypt(flag_enc))
#b'NCTF{1t_7urn3d_0u7_7h47_u_2_g00d_@_r3v3rs3_1snt}'
145.[INSHack2018]Crypt0r part 1
查看题目
# Crypt0r part 1
Our IDS detected an abnormal behavior from one of our user. We extracted this pcap, could you have a look at it?
<a href="http://crypt0r.challenge-by.ovh/ids_alert_24032018.pcap">http://crypt0r.challenge-by.ovh/ids_alert_24032018.pcap</a>下载后是个cap。打开后流量很简单,直接跟踪TCP流,得到
CRYPT0R_SEED:58
CRYPT0R:PMSFADNIJKBXQCGYWETOVHRULZSELYO0E_PSB
SELYO0E:PXX_NGGFSELYO0E:NAO_HJSOJQ_JF>{A2FS3118-0399-48S7-857S-43D9528DD98F}
SELYO0E:HJSOJQ_JF_JT>....SELYO0E:NAO_DJCPX_QTN
SELYO0E:DJCPX_QTN_JT>!!! PXX LGVE DJXAT IPHA MAAC ACSELYOAF !!!Selyo0e toegba mpsb pcf lgv ngo dvsb*f mvffl. Lgv spccgo faselyo lgve fpop ausayo jd lgv ypl qa $500. #TIGRQAOIAQGCAL pcf J rjxx njha lgv mpsb lgve fpop.Dgxxgr oiata jctoevsojgct:
- Jctopxx oia oge megrtae, pcf ng og gve yplqaco yxpodgeq: iooy://bu4ifi2zg5etosvk.gcjgc (YSJ-FTT pyyeghaf gds meg).
- Acoae lgve yaetgcpx bal: JCTP{mW9CLVlPjpUtbZFdccPioVV01jdaUeGv}Oipcbt dge vtjcn ql epctgqrpea.Rjoi xgha,
Selyo0qpc
string1 = "PMSFADNIJKBXQCGYWETOVHRULZpmsfadnijkbxqcgywetovhrulz"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz"
str1 = """
CRYPT0R_SEED:58
CRYPT0R:PMSFADNIJKBXQCGYWETOVHRULZSELYO0E_PSB
SELYO0E:PXX_NGGFSELYO0E:NAO_HJSOJQ_JF>{A2FS3118-0399-48S7-857S-43D9528DD98F}
SELYO0E:HJSOJQ_JF_JT>....SELYO0E:NAO_DJCPX_QTN
SELYO0E:DJCPX_QTN_JT>!!! PXX LGVE DJXAT IPHA MAAC ACSELYOAF !!!Selyo0e toegba mpsb pcf lgv ngo dvsb*f mvffl. Lgv spccgo faselyo lgve fpop ausayo jd lgv ypl qa $500. #TIGRQAOIAQGCAL pcf J rjxx njha lgv mpsb lgve fpop.Dgxxgr oiata jctoevsojgct:
- Jctopxx oia oge megrtae, pcf ng og gve yplqaco yxpodgeq: iooy://bu4ifi2zg5etosvk.gcjgc (YSJ-FTT pyyeghaf gds meg).
- Acoae lgve yaetgcpx bal: JCTP{mW9CLVlPjpUtbZFdccPioVV01jdaUeGv}Oipcbt dge vtjcn ql epctgqrpea.Rjoi xgha,
Selyo0qpc
"""
print (str1.translate(str.maketrans(string1,string2)))
运行得到
NWPAS0W_CRRF:58
NWPAS0W:ABCDEFGHIJKLMNOPQRSTUVWXYZCRYPT0R_ACK
CRYPT0R:ALL_GOODCRYPT0R:GET_VICTIM_ID>{E2DC3118-0399-48C7-857C-43F9528FF98D}
CRYPT0R:VICTIM_ID_IS>....CRYPT0R:GET_FINAL_MSG
CRYPT0R:FINAL_MSG_IS>!!! ALL YOUR FILES HAVE BEEN ENCRYPTED !!!Crypt0r stroke back and you got fuck*d buddy. You cannot decrypt your data except if you pay me $500. #SHOWMETHEMONEY and I will give you back your data.Follow these instructions:
- Install the tor browser, and go to our payment platform: http://kx4hdh2zo5rstcuj.onion (PCI-DSS approved ofc bro).
- Enter your personal key: INSA{bQ9NYUyAiaXskZDfnnAhtUU01ifeXrOu}Thanks for using my ransomware.With love,
Crypt0man进程完成,退出码 0key就是flag
146.[XNUCA2018]baby_crypto
查看题目
The 26 letters a, b, c, ..., y, z correspond to the integers 0, 1, 2, ..., 25
len(key_a) = m
len(key_k) = n
c[i] = (p[i] * key_a[i % m] + key_k[i % n]) % 26p is plain text, only lowercase letters are refered to.
c is encrypted textI have appended the flag at the end of plain text, the format of which is like 'flagis......'
Now you have the encrypted text, Good luck!
看了两个大佬的wp1,wp2总结得到下面的脚本
#重合指数的应用:
import gmpy2
c=open('encrypted_message.txt','r').read()
best_index=0.065
sum=0
dic_index={'a': 0.08167,'b': 0.01492,'c': 0.02782,'d':0.04253,'e': 0.12702,'f':0.02228,'g': 0.02015,'h':0.06094,'i':0.06966,'j':0.00153,'k':0.00772,'l':0.04025,'m':0.02406,'n':0.06749,'o':0.07507,'p':0.01929,'q':0.00095,'r':0.05987,'s':0.06327,'t':0.09056,'u':0.02758,'v':0.00978,'w':0.02360,'x':0.00150,'y':0.01974,'z':0.00074}
def index_of_coincidence(s):'''计算字符串的重合指数(所有字母出现频率的平方和):param s: 给定字符串:return: 重合指数'''alpha='abcdefghijklmnopqrstuvwxyz'#给定字母表freq={}#统计字母频率(frequency)for i in alpha:freq[i]=0#先全部初始化为0for i in s:freq[i]=freq[i]+1#统计频率index=0for i in alpha:index = index + (freq[i] * (freq[i] - 1)) / (len(s) * (len(s) - 1))return index
def index_of_coincidence_m(s):'''计算明文s中的各字母的频率与英文字母中的频率的吻合程度.:param s:明文s:return:吻合程度'''alpha = 'abcdefghijklmnopqrstuvwxyz' # 给定字母表freq = {} # 统计字母频率(frequency)for i in alpha:freq[i] = 0# 先全部初始化为0for i in s:freq[i] = freq[i] + 1# 统计频率index = 0for i in alpha:index = index + freq[i] / len(s) * dic_index[i]return index
def get_cycle(c):'''求出最符合统计学的m,n的最小公共周期,方法为通过爆破足够大的周期样本,观察成倍出现的周期.计算方法为解出每一个子密文段的重合指数和然后求平均值 再与最佳重合指数相减 误差在0.01以内.:param c: 密文:return: 公共周期列表'''cycle=[]for i in range(1,100):average_index=0#平均重合指数初始化为0for j in range(i):s = ''.join(c[j+i*x] for x in range(0,len(c)//i))index=index_of_coincidence(s)average_index+=indexaverage_index=average_index/i-best_indexif abs(average_index)<0.01:cycle.append(i)return cycle
cycle=get_cycle(c)
print(cycle)#[6, 12, 18, 24, 30, 36, 42, 48, 54, 60, 66, 72, 78, 84, 90, 96]#通过计算得到cycle都是6的倍数,因此cycle最小很有可能为6cycle=6#开始爆破keysdef decrypt(c,i,j):'''通过i,j解出与之相对应的密文段:param c: 密文段:param i:与明文相乘的key:param j: 位移j(维吉尼亚密码):return: 明文段'''alpha = 'abcdefghijklmnopqrstuvwxyz'm=''for x in c:m+=alpha[((alpha.index(x)-j)*gmpy2.invert(i,26))%26]return m
def get_key(c):'''得到某一密文段的单个字符key i j方法为暴力枚举所有的可能性,找到最符合统计学规律的 i,j 即该密文段的重合指数与最佳重合指数误差小于0.01:param c: 密文段:return: i,j'''for i in range(26):if gmpy2.gcd(i,26)!=1:#i对26的逆元不只一个,造成明文不唯一,因此不符合条件.continuefor j in range(26):m=decrypt(c,i,j)index=index_of_coincidence_m(m)if abs(index-0.065)<0.01:return (i,j)
def get_all_key(s,cycle):'''得到一个周期内的所有的密文段的key:param s: 原密文:param cycle: 周期:return: 无'''for i in range(cycle):temps=''.join([s[i+x*cycle] for x in range(0,len(s)//cycle)])print(get_key(temps))
get_all_key(c,6)
# (19, 10)
# (7, 9)
# (23, 3)
# (19, 24)
# (7, 14)
# (23, 15)
#此时我们大致可以推测出:keya=[19,7,23],keyb=[10,9,3,24,14,15],因此根据题目给的式子,我们就可以还原出明文了.
plaintext=''
keya=[19,7,23]
keyb=[10,9,3,24,14,15]
len_a=len(keya)
len_b=len(keyb)
alpha='abcdefghijklmnopqrstuvwxyz'
for i in range(len(c)):plaintext+=alpha[((alpha.index(c[i])-keyb[i%len_b])*gmpy2.invert(keya[i%len_a],26))%26]
print(plaintext)
#sandandfoambykahlilgibraniamforeverwalkingupontheseshoresbetwixtthesandandthefoamthehightidewillerasemyfootprintsandthewindwillblowawaythefoambuttheseaandtheshorewillremainforeveronceifilledmyhandwithmisttheniopeneditandlothemistwasawormandiclosedandopenedmyhandagainandbeholdtherewasabirdandagainiclosedandopenedmyhandandinitshollowstoodamanwithasadfaceturnedupwardandagainiclosedmyhandandwheniopenedittherewasnaughtbutmistbutiheardasongofexceedingsweetnessitwasbutyesterdayithoughtmyselfafragmentquiveringwithoutrhythminthesphereoflifenowiknowthatiamthesphereandalllifeinrhythmicfragmentsmoveswithinmetheysaytomeintheirawakeningyouandtheworldyouliveinarebutagrainofsandupontheinfiniteshoreofaninfiniteseaandinmydreamisaytothemiamtheinfiniteseaandallworldsarebutgrainsofsanduponmyshoreonlyoncehaveibeenmademuteitwaswhenamanaskedmewhoareyouthefirstthoughtofgodwasanangelthefirstwordofgodwasamanwewereflutteringwanderinglongingcreaturesathousandthousandyearsbeforetheseaandthewindintheforestgaveuswordsnowhowcanweexpresstheancientofdaysinuswithonlythesoundsofouryesterdaysthesphinxspokeonlyonceandthesphinxsaidagrainofsandisadesertandadesertisagrainofsandandnowletusallbesilentagainiheardthesphinxbutididnotunderstandlongdidilieinthedustofegyptsilentandunawareoftheseasonsthenthesungavemebirthandiroseandwalkeduponthebanksofthenilesingingwiththedaysanddreamingwiththenightsandnowthesunthreadsuponmewithathousandfeetthatimaylieagaininthedustofegyptbutbeholdamarvelandariddletheverysunthatgatheredmecannotscattermestillerectamiandsureoffootdoiwalkuponthebanksofthenileremembranceisaformofmeetingforgetfulnessisaformoffreedomwemeasuretimeaccordingtothemovementofcountlesssunsandtheymeasuretimebylittlemachinesintheirlittlepocketsnowtellmehowcouldweevermeetatthesameplaceandthesametimespaceisnotspacebetweentheearthandthesuntoonewholooksdownfromthewindowsofthemilkywayhumanityisariveroflightrunningfromtheexeternitytoeternitydonotthespiritswhodwellintheetherenvymanhispainonmywaytotheholycityimetanotherpilgrimandiaskedhimisthisindeedthewaytotheholycityandhesaidfollowmeandyouwillreachtheholycityinadayandanightandifollowedhimandwewalkedmanydaysandmanynightsyetwedidnotreachtheholycityandwhatwastomysurprisehebecameangrywithmebecausehehadmisledmemakemeohgodthepreyofthelionereyoumaketherabbitmypreyonemaynotreachthedawnsavebythepathofthenightmyhousesaystomedonotleavemeforheredwellsyourpastandtheroadsaystomecomeandfollowmeforiamyourfutureandisaytobothmyhouseandtheroadihavenopastnorhaveiafutureifistayherethereisagoinginmystayingandifigothereisastayinginmygoingonlyloveanddeathwillchangeallthingshowcanilosefaithinthejusticeoflifewhenthedreamsofthosewhosleepuponfeathersarenotmorebeautifulthanthedreamsofthosewhosleepupontheearthstrangethedesireforcertainpleasuresisapartofmypainseventimeshaveidespisedmysoulthefirsttimewhenisawherbeingmeekthatshemightattainheightthesecondtimewhenisawherlimpingbeforethecrippledthethirdtimewhenshewasgiventochoosebetweenthehardandtheeasyandshechosetheeasythefourthtimewhenshecommittedawrongandcomfortedherselfthatothersalsocommitwrongthefifthtimewhensheforboreforweaknessandattributedherpatiencetostrengththesixthtimewhenshedespisedtheuglinessofafaceandknewnotthatitwasoneofherownmasksandtheseventhtimewhenshesangasongofpraiseanddeemeditavirtueiamignorantofabsolutetruthbutiamhumblebeforemyignoranceandthereinliesmyhonorandmyrewardthereisaspacebetweenmansimaginationandmansattainmentthatmayonlybetraversedbyhislongingparadiseistherebehindthatdoorinthenextroombutihavelostthekeyperhapsihaveonlymislaidityouareblindandiamdeafanddumbsoletustouchhandsandunderstandthesignificanceofmanisnotinwhatheattainsbutratherinwhathelongstoattainsomeofusarelikeinkandsomelikepaperandifitwerenotfortheblacknessofsomeofussomeofuswouldbedumbandifitwerenotforthewhitenessofsomeofussomeofuswouldbeblindgivemeanearandiwillgiveyouavoiceourmindisaspongeourheartisastreamisitnotstrangethatmostofuschoosesuckingratherthanrunningwhenyoulongforblessingsthatyoumaynotnameandwhenyougrieveknowingnotthecausethenindeedyouaregrowingwithallthingsthatgrowandrisingtowardyourgreaterselfwhenoneisdrunkwithavisionhedeemshisfaintexpressionofittheverywineyoudrinkwinethatyoumaybeintoxicatedandidrinkthatitmaysobermefromthatotherwinewhenmycupisemptyiresignmyselftoitsemptinessbutwhenitishalffulliresentitshalffulnesstherealityoftheotherpersonisnotinwhatherevealstoyoubutinwhathecannotrevealtoyouthereforeifyouwouldunderstandhimlistennottowhathesaysbutrathertowhathedoesnotsayhalfofwhatisayismeaninglessbutisayitsothattheotherhalfmayreachyouasenseofhumourisasenseofproportionmylonelinesswasbornwhenmenpraisedmytalkativefaultsandblamedmysilentvirtueswhenlifedoesnotfindasingertosingherheartsheproducesaphilosophertospeakhermindatruthistobeknownalwaystobeutteredsometimestherealinusissilenttheacquiredistalkativethevoiceoflifeinmecannotreachtheearoflifeinyoubutletustalkthatwemaynotfeellonelywhentwowomentalktheysaynothingwhenonewomanspeakssherevealsalloflifefrogsmaybellowlouderthanbullsbuttheycannotdragtheploughinthefieldnotturnthewheelofthewinepressandoftheirskinsyoucannotmakeshoesonlythedumbenvythetalkativeifwintershouldsayspringisinmyheartwhowouldbelievewintereveryseedisalongingshouldyoureallyopenyoureyesandseeyouwouldbeholdyourimageinallimagesandshouldyouopenyourearsandlistenyouwouldhearyourownvoiceinallvoicesittakestwoofustodiscovertruthonetoutteritandonetounderstanditthoughthewaveofwordsisforeveruponusyetourdepthisforeversilentmanyadoctrineislikeawindowpaneweseetruththroughitbutitdividesusfromtruthnowletusplayhideandseekshouldyouhideinmyheartitwouldnotbedifficulttofindyoubutshouldyouhidebehindyourownshellthenitwouldbeuselessforanyonetoseekyouawomanmayveilherfacewithasmilehownobleisthesadheartwhowouldsingajoyoussongwithjoyousheartshewhowouldunderstandawomanordissectgeniusorsolvethemysteryofsilenceistheverymanwhowouldwakefromabeautifuldreamtositatabreakfasttableiwouldwalkwithallthosewhowalkiwouldnotstandstilltowatchtheprocessionpassingbyyouowemorethangoldtohimwhoservesyougivehimofyourheartorservehimnaywehavenotlivedinvainhavetheynotbuilttowersofourbonesletusnotbeparticularandsectionalthepoetsmindandthescorpionstailriseingloryfromthesameeartheverydragongivesbirthtoastgeorgewhoslaysittreesarepoemsthattheearthwritesupontheskywefellthemdownandturnthemintopaperthatwemayrecordouremptinessshouldyoucaretowriteandonlythesaintsknowwhyyoushouldyoumustneedshaveknowledgeandartandmusictheknowledgeofthemusicofwordstheartofbeingartlessandthemagicoflovingyourreaderstheydiptheirpensinourheartsandthinktheyareinspiredshouldatreewriteitsautobiographyitwouldnotbeunlikethehistoryofaraceifiweretochoosebetweenthepowerofwritingapoemandtheecstasyofapoemunwritteniwouldchoosetheecstasyitisbetterpoetrybutyouandallmyneighborsagreethatialwayschoosebadlypoetryisnotanopinionexpresseditisasongthatrisesfromableedingwoundorasmilingmouthwordsaretimelessyoushouldutterthemorwritethemwithaknowledgeoftheirtimelessnessapoetisadethronedkingsittingamongtheashesofhispalacetryingtofashionanimageoutoftheashespoetryisadealofjoyandpainandwonderwithadashofthedictionaryinvainshallapoetseekthemotherofthesongsofhisheartonceisaidtoapoetweshallnotknowyourworthuntilyoudieandheansweredsayingyesdeathisalwaystherevealerandifindeedyouwouldknowmyworthitisthatihavemoreinmyheartthanuponmytongueandmoreinmydesirethaninmyhandifyousingofbeautythoughaloneintheheartofthedesertyouwillhaveanaudiencepoetryiswisdomthatenchantstheheartwisdomispoetrythatsingsinthemindifwecouldenchantmansheartandatthesametimesinginhismindthenintruthhewouldliveintheshadowofgodinspirationwillalwayssinginspirationwillneverexplainweoftensinglullabiestoourchildrenthatweourselvesmaysleepallourwordsarebutcrumbsthatfalldownfromthefeastofthemindthinkingisalwaysthestumblingstonetopoetryagreatsingerishewhosingsoursilenceshowcanyousingifyourmouthbefilledwithfoodhowshallyourhandberaisedinblessingifitisfilledwithgoldtheysaythenightingalepierceshisbosomwithathornwhenhesingshislovesongsodoweallhowelseshouldwesinggeniusisbutarobinssongatthebeginningofaslowspringeventhemostwingedspiritcannotescapephysicalnecessityamadmanisnotlessamusicianthanyouormyselfonlytheinstrumentonwhichheplaysisalittleoutoftunethesongthatliessilentintheheartofamothersingsuponthelipsofherchildnolongingremainsunfulfilledihaveneveragreedwithmyotherselfwhollythetruthofthematterseemstoliebetweenusyourotherselfisalwayssorryforyoubutyourotherselfgrowsonsorrowsoalliswellthereisnostruggleofsoulandbodysaveinthemindsofthosewhosesoulsareasleepandwhosebodiesareoutoftunewhenyoureachtheheartoflifeyoushallfindbeautyinallthingsevenintheeyesthatareblindtobeautyweliveonlytodiscoverbeautyallelseisaformofwaitingsowaseedandtheearthwillyieldyouaflowerdreamyourdreamtotheskyanditwillbringyouyourbelovedthedevildiedtheverydayyouwerebornnowyoudonothavetogothroughhelltomeetanangelmanyawomanborrowsamansheartveryfewcouldpossessitifyouwouldpossessyoumustnotclaimwhenamanshandtouchesthehandofawomantheybothtouchtheheartofeternityloveistheveilbetweenloverandlovereverymanlovestwowomentheoneisthecreationofhisimaginationandtheotherisnotyetbornmenwhodonotforgivewomentheirlittlefaultswillneverenjoytheirgreatvirtueslovethatdoesnotrenewitselfeverydaybecomesahabitandinturnaslaveryloversembracethatwhichisbetweenthemratherthaneachotherloveanddoubthaveneverbeenonspeakingtermsloveisawordoflightwrittenbyahandoflightuponapageoflightfriendshipisalwaysasweetresponsibilityneveranopportunityifyoudonotunderstandyourfriendunderallconditionsyouwillneverunderstandhimyourmostradiantgarmentisoftheotherpersonsweavingyoumostsavorymealisthatwhichyoueatattheotherpersonstableyourmostcomfortablebedisintheotherpersonshousenowtellmehowcanyouseparateyourselffromtheotherpersonyourmindandmyheartwillneveragreeuntilyourmindceasestoliveinnumbersandmyheartinthemistweshallneverunderstandoneanotheruntilwereducethelanguagetosevenwordshowshallmyheartbeunsealedunlessitbebrokenonlygreatsorroworgreatjoycanrevealyourtruthifyouwouldberevealedyoumusteitherdancenakedinthesunorcarryyourcrossshouldnatureheedwhatwesayofcontentmentnoriverwouldseektheseaandnowinterwouldturntospringshouldsheheedallwesayofthrifthowmanyofuswouldbebreathingthisairyouseebutyourshadowwhenyouturnyourbacktothesunyouarefreebeforethesunofthedayandfreebeforethestarsofthenightandyouarefreewhenthereisnosunandnomoonandnostaryouareevenfreewhenyoucloseyoureyesuponallthereisbutyouareaslavetohimwhomyoulovebecauseyoulovehimandaslavetohimwholovesyoubecausehelovesyouweareallbeggarsatthegateofthetempleandeachoneofusreceiveshisshareofthebountyofthekingwhenheentersthetempleandwhenhegoesoutbutwearealljealousofoneanotherwhichisanotherwayofbelittlingthekingyoucannotconsumebeyondyourappetitetheotherhalfoftheloafbelongstotheotherpersonandthereshouldremainalittlebreadforthechanceguestifitwerenotforyourguestsallhouseswouldbegravessaidagraciouswolftoasimplesheepwillyounothonorourhousewithavisitandthesheepansweredwewouldhavebeenhonoredtovisityourhouseifitwerenotinyourstomachistoppedmyguestonthethresholdandsaidnaywipenotyourfeetasyouenterbutasyougooutgenerosityisnotingivingmethatwhichineedmorethanyoudobutitisingivingmethatwhichyouneedmorethanidoyouareindeedcharitablewhenyougiveandwhilegivingturnyourfaceawaysothatyoumaynotseetheshynessofthereceiverthedifferencebetweentherichestmanandthepoorestisbutadayofhungerandanhourofthirstweoftenborrowfromourtomorrowstopayourdebtstoouryesterdaysitooamvisitedbyangelsanddevilsbutigetridofthemwhenitisanangeliprayanoldprayerandheisboredwhenitisadevilicommitanoldsinandhepassesmebyafterallthisisnotabadprisonbutidonotlikethiswallbetweenmycellandthenextprisonerscellyetiassureyouthatidonotwishtoreproachthewardernotthebuilderoftheprisonthosewhogiveyouaserpentwhenyouaskforafishmayhavenothingbutserpentstogiveitisthengenerosityontheirparttrickerysucceedssometimesbutitalwayscommitssuicideyouaretrulyaforgiverwhenyouforgivemurdererswhoneverspillbloodthieveswhoneverstealandliarswhoutternofalsehoodhewhocanputhisfingeruponthatwhichdividesgoodfromevilishewhocantouchtheveryhemofthegarmentofgodifyourheartisavolcanohowshallyouexpectflowerstobloominyourhandsastrangeformofselfindulgencetherearetimeswheniwouldbewrongedandcheatedthatimaylaughattheexpenseofthosewhothinkidonotknowiambeingwrongedandcheatedwhatshallisayofhimwhoisthepursuerplayingthepartofthepursuedlethimwhowipeshissoiledhandswithyourgarmenttakeyourgarmenthemayneeditagainsurelyyouwouldnotitisapitythatmoneychangerscannotbegoodgardenerspleasedonotwhitewashyourinherentfaultswithyouracquiredvirtuesiwouldhavethefaultstheyarelikemineownhowoftenhaveiattributedtomyselfcrimesihavenevercommittedsothattheotherpersonmayfeelcomfortableinmypresenceeventhemasksoflifearemasksofdeepermysteryyoumayjudgeothersonlyaccordingtoyourknowledgeofyourselftellmenowwhoamongusisguiltyandwhoisunguiltythetrulyjustishewhofeelshalfguiltyofyourmisdeedsonlyanidiotandageniusbreakmanmadelawsandtheyarethenearesttotheheartofgoditisonlywhenyouarepursuedthatyoubecomeswiftihavenoenemiesogodbutifiamtohaveanenemylethisstrengthbeequaltominethattruthalonemaybethevictoryouwillbequitefriendlywithyourenemywhenyoubothdieperhapsamanmaycommitsuicideinselfdefenselongagotherelivedamanwhowascrucifiedforbeingtoolovingandtoolovableandstrangetorelateimethimthriceyesterdaythefirsttimehewasaskingapolicemannottotakeaprostitutetoprisonthesecondtimehewasdrinkingwinewithanoutcastandthethirdtimehewashavingafistfightwithapromoterinsideachurchifalltheysayofgoodandevilweretruethenmylifeisbutonelongcrimepityisbuthalfjusticetheonlyonewhohasbeenunjusttomeistheonetowhosebrotherihavebeenunjustwhenyouseeamanledtoprisonsayinyourheartmayhapheisescapingfromanarrowerprisonandwhenyouseeamandrunkensayinyourheartmayhaphesoughtescapefromsomethingstillmoreunbeautifuloftentimesihavehatedinselfdefensebutifiwerestrongeriwouldnothaveusedsuchaweaponhowstupidishewhowouldpatchthehatredinhiseyeswiththesmileofhislipsonlythosebeneathmecanenvyorhatemeihaveneverbeenenviednorhatediamabovenooneonlythoseabovemecanpraiseorbelittlemeihaveneverbeenpraisednorbelittlediambelownooneyoursayingtomeidonotunderstandyouispraisebeyondmyworthandaninsultyoudonotdeservehowmeanamiwhenlifegivesmegoldandigiveyousilverandyetideemmyselfgenerouswhenyoureachtheheartoflifeyouwillfindyourselfnothigherthanthefelonandnotlowerthantheprophetstrangethatyoushouldpitytheslowfootedandnottheslowmindedandtheblindeyedratherthantheblindhearteditiswiserforthelamenottobreakhiscrutchesupontheheadofhisenemyhowblindishewhogivesyououtofhispocketthathemaytakeoutofyourheartlifeisaprocessiontheslowoffootfindsittooswiftandhestepsoutandtheswiftoffootfindsittooslowandhetoostepsoutifthereissuchathingassinsomeofuscommititbackwardfollowingourforefathersfootstepsandsomeofuscommititforwardbyoverrulingourchildrenthetrulygoodishewhoisonewithallthosewhoaredeemedbadweareallprisonersbutsomeofusareincellswithwindowsandsomewithoutstrangethatwealldefendourwrongswithmorevigorthanwedoourrightsshouldweallconfessoursinstooneanotherwewouldalllaughatoneanotherforourlackoforiginalityshouldweallrevealourvirtueswewouldalsolaughforthesamecauseanindividualisabovemanmadelawsuntilhecommitsacrimeagainstmanmadeconventionsafterthatheisneitheraboveanyonenorlowerthananyonegovernmentisanagreementbetweenyouandmyselfyouandmyselfareoftenwrongcrimeiseitheranothernameofneedoranaspectofadiseaseisthereagreaterfaultthanbeingconsciousoftheotherpersonsfaultsiftheotherpersonlaughsatyouyoucanpityhimbutifyoulaughathimyoumayneverforgiveyourselfiftheotherpersoninjuresyouyoumayforgettheinjurybutifyouinjurehimyouwillalwaysrememberintruththeotherpersonisyourmostsensitiveselfgivenanotherbodyhowheedlessyouarewhenyouwouldhavemenflywithyourwingsandyoucannotevengivethemafeatheronceamansatatmyboardandatemybreadanddrankmywineandwentawaylaughingatmethenhecameagainforbreadandwineandispurnedhimandtheangelslaughedatmehateisadeadthingwhoofyouwouldbeatombitisthehonorofthemurderedthatheisnotthemurdererthetribuneofhumanityisinitssilentheartneveritstalkativemindtheydeemmemadbecauseiwillnotsellmydaysforgoldandideemthemmadbecausetheythinkmydayshaveapricetheyspreadbeforeustheirrichesofgoldandsilverofivoryandebonyandwespreadbeforethemourheartsandourspiritsandyettheydeemthemselvesthehostsandustheguestsiwouldnotbetheleastamongmenwithdreamsandthedesiretofulfillthemratherthanthegreatestwithnodreamsandnodesiresthemostpitifulamongmenishewhoturnshisdreamsintosilverandgoldweareallclimbingtowardthesummitofourheartsdesireshouldtheotherclimberstealyoursackandyourpurseandwaxfatontheoneandheavyontheotheryoushouldpityhimtheclimbingwillbeharderforhisfleshandtheburdenwillmakehiswaylongerandshouldyouinyourleannessseehisfleshpuffingupwardhelphimastepitwilladdtoyourswiftnessyoucannotjudgeanymanbeyondyourknowledgeofhimandhowsmallisyourknowledgeiwouldnotlistentoaconquerorpreachingtotheconqueredthetrulyfreemanishewhobearstheloadofthebondslavepatientlyathousandyearsagomyneighborsaidtomeihatelifeforitisnaughtbutathingofpainandyesterdayipassedbyacemeteryandsawlifedancinguponhisgravestrifeinnatureisbutdisorderlongingforordersolitudeisasilentstormthatbreaksdownallourdeadbranchesyetitsendsourlivingrootsdeeperintothelivingheartofthelivingearthonceispokeoftheseatoabrookandthebrookthoughtmebutanimaginativeexaggeratorandonceispokeofabrooktotheseaandtheseathoughtmebutadepreciativedefamerhownarrowisthevisionthatexaltsthebusynessoftheantabovethesingingofthegrasshopperthehighestvirtueheremaybetheleastinanotherworldthedeepandthehighgotothedepthortotheheightinastraightlineonlythespaciouscanmoveincirclesifitwerenotforourconceptionofweightsandmeasureswewouldstandinaweofthefireflyaswedobeforethesunascientistwithoutimaginationisabutcherwithdullknivesandoutwornscalesbutwhatwouldyousincewearenotallvegetarianswhenyousingthehungryhearsyouwithhisstomachdeathisnotnearertotheagedthantothenewbornneitherislifeifindeedyoumustbecandidbecandidbeautifullyotherwisekeepsilentforthereisamaninourneighborhoodwhoisdyingmayhapafuneralamongmenisaweddingfeastamongtheangelsaforgottenrealitymaydieandleaveinitswillseventhousandactualitiesandfactstobespentinitsfuneralandthebuildingofatombintruthwetalkonlytoourselvesbutsometimeswetalkloudenoughthatothersmayhearustheobviousisthatwhichisneverseenuntilsomeoneexpressesitsimplyifthemilkywaywerenotwithinmehowshouldihaveseenitorknownitunlessiamaphysicianamongphysicianstheywouldnotbelievethatiamanastronomerperhapstheseasdefinitionofashellisthepearlperhapstimesdefinitionofcoalisthediamondfameistheshadowofpassionstandinginthelightarootisaflowerthatdisdainsfamethereisneitherreligionnorsciencebeyondbeautyeverygreatmanihaveknownhadsomethingsmallinhismakeupanditwasthatsmallsomethingwhichpreventedinactivityormadnessorsuicidethetrulygreatmanishewhowouldmasternooneandwhowouldbemasteredbynoneiwouldnotbelievethatamanismediocresimplybecausehekillsthecriminalsandtheprophetstoleranceislovesickwiththesicknessofhaughtinesswormswillturnbutisitnotstrangethatevenelephantswillyieldadisagreementmaybetheshortestcutbetweentwomindsiamtheflameandiamthedrybushandonepartofmeconsumestheotherpartweareallseekingthesummitoftheholymoutainbutshallnotourroadbeshorterifweconsiderthepastachartandnotaguidewisdomceasestobewisdomwhenitbecomestooproudtoweeptoogravetolaughandtooselffultoseekotherthanitselfhadifilledmyselfwithallthatyouknowwhatroomshouldihaveforallthatyoudonotknowihavelearnedsilencefromthetalkativetolerationfromtheintolerantandkindnessfromtheunkindyetstrangeiamungratefultotheseteachersabigotisastoneleaforatorthesilenceoftheenviousistoonoisywhenyoureachtheendofwhatyoushouldknowyouwillbeatthebeginningofwhatyoushouldsenseanexaggerationisatruththathaslostitstemperifyoucanseeonlywhatlightrevealsandhearonlywhatsoundannouncesthenintruthyoudonotseenordoyouhearafactisatruthunsexedyoucannotlaughandbeunkindatthesametimethenearesttomyheartareakingwithoutakingdomandapoormanwhodoesnotknowhowtobegashyfailureisnoblerthananimmodestsuccessdiganywhereintheearthandyouwillfindatreasureonlyyoumustdigwiththefaithofapeasantsaidahuntedfoxfollowedbytwentyhorsemenandapackoftwentyhoundsofcoursetheywillkillmebuthowpoorandhowstupidtheymustbesurelyitwouldnotbeworthwhilefortwentyfoxesridingontwentyassesandaccompaniedbytwentywolvestochaseandkillonemanitisthemindinusthatyieldstothelawsmadebyusbutneverthespiritinusatraveleramiandanavigatorandeverydayidiscoveranewregionwithinmysoulawomanprotestedsayingofcourseitwasarighteouswarmysonfellinitisaidtolifeiwouldheardeathspeakandliferaisedhervoicealittlehigherandsaidyouhearhimnowwhenyouhavesolvedallthemysteriesoflifeyoulongfordeathforitisbutanothermysteryoflifebirthanddeatharethetwonoblestexpressionsofbraverymyfriendyouandishallremainstrangersuntolifeanduntooneanotherandeachuntohimselfuntilthedaywhenyoushallspeakandishalllistendeemingyourvoicemyownvoiceandwhenishallstandbeforeyouthinkingmyselfstandingbeforeamirrortheysaytomeshouldyouknowyourselfyouwouldknowallmenandisayonlywheniseekallmenshalliknowmyselfmanistwomenoneisawakeindarknesstheotherisasleepinlightahermitisonewhorenouncestheworldoffragmentsthathemayenjoytheworldwhollyandwithoutinterruptionthereliesagreenfieldbetweenthescholarandthepoetshouldthescholarcrossithebecomesawisemanshouldthepoetcrossithebecomesaprophetyestereveisawphilosophersinthemarketplacecarryingtheirheadsinbasketsandcryingaloudwisdomwisdomforsalepoorphilosopherstheymustneedsselltheirheadstofeedtheirheartssaidaphilosophertoastreetsweeperipityyouyoursisahardanddirtytaskandthestreetsweepersaidthankyousirbuttellmewhatisyourtaskandthephilosopheransweredsayingistudymansmindhisdeedsandhisdesiresthenthestreetsweeperwentonwithhissweepingandsaidwithasmileipityyoutoohewholistenstotruthisnotlessthanhewhoutterstruthnomancandrawthelinebetweennecessitiesandluxuriesonlytheangelscandothatandtheangelsarewiseandwistfulperhapstheangelsareourbetterthoughtinspaceheisthetrueprincewhofindshisthroneintheheartofthedervishgenerosityisgivingmorethanyoucanandprideistakinglessthanyouneedintruthyouowenaughttoanymanyouowealltoallmenallthosewhohavelivedinthepastlivewithusnowsurelynoneofuswouldbeanungracioushosthewholongsthemostlivesthelongesttheysaytomeabirdinthehandisworthteninthebushbutisayabirdandafeatherinthebushisworthmorethantenbirdsinthehandyourseekingafterthatfeatherislifewithwingedfeetnayitislifeitselfthereareonlytwoelementsherebeautyandtruthbeautyintheheartsofloversandtruthinthearmsofthetillersofthesoilgreatbeautycapturesmebutabeautystillgreaterfreesmeevenfromitselfbeautyshinesbrighterintheheartofhimwholongsforitthanintheeyesofhimwhoseesitiadmirehimwhorevealshismindtomeihonorhimwhounveilshisdreamsbutwhyamishyandevenalittleashamedbeforehimwhoservesmethegiftedwereonceproudinservingprincesnowtheyclaimhonorinservingpauperstheangelsknowthattoomanypracticalmeneattheirbreadwiththesweatofthedreamersbrowwitisoftenamaskifyoucouldtearityouwouldfindeitherageniusirritatedorclevernessjugglingtheunderstandingattributestomeunderstandingandthedulldullnessithinktheyarebothrightonlythosewithsecretsintheirheartscoulddivinethesecretsinourheartshewhowouldshareyourpleasurebutnotyourpainshalllosethekeytooneofthesevengatesofparadiseyesthereisanirvanahitisinleadingyoursheeptoagreenpastureandinputtingyourchildtosleepandinwritingthelastlineofyourpoemwechooseourjoysandoursorrowslongbeforeweexperiencethemsadnessisbutawallbetweentwogardenswheneitheryourjoyoryoursorrowbecomesgreattheworldbecomessmalldesireishalfoflifeidifferenceishalfofdeaththebitterestthinginourtodayssorrowisthememoryofouryesterdaysjoytheysaytomeyoumustneedschoosebetweenthepleasuresofthisworldandthepeaceofthenextworldandisaytothemihavechosenboththedelightsofthisworldandthepeaceofthenextforiknowinmyheartthatthesupremepoetwrotebutonepoemanditscansperfectlyanditalsorhymesperfectlyfaithisanoasisintheheartwhichwillneverbereachedbythecaravanofthinkingwhenyoureachyourheightyoushalldesirebutonlyfordesireandyoushallhungerforhungerandyoushallthirstforgreaterthirstifyourevealyoursecretstothewindyoushouldnotblamethewindforrevealingthemtothetreestheflowersofspringarewintersdreamsrelatedatthebreakfasttableoftheangelssaidaskunktoatuberoseseehowswiftlyirunwhileyoucannotwalknorevencreepsaidthetuberosetotheskunkohmostnobleswiftrunnerpleaserunswiftlyturtlescantellmoreaboutroadsthanharesstrangethatcreatureswithoutbackboneshavethehardestshellsthemosttalkativeistheleastintelligentandthereishardlyadifferencebetweenanoratorandanauctioneerbegratefulthatyoudonothavetolivedowntherenownofafathernorthewealthofanunclebutaboveallbegratefulthatnoonewillhavetolivedowneitheryourrenownoryourwealthonlywhenajugglermissescatchinghisballdoesheappealtometheenviouspraisesmeunknowinglylongwereyouadreaminyourmotherssleepandthenshewoketogiveyoubirththegermoftheraceisinyourmotherslongingmyfatherandmotherdesiredachildandtheybegotmeandiwantedamotherandafatherandibegotnightandtheseasomeofourchildrenareourjustificationsandsomearebutourregretswhennightcomesandyoutooaredarkliedownandbedarkwithawillandwhenmorningcomesandyouarestilldarkstandupandsaytothedaywithawilliamstilldarkitisstupidtoplayarolewiththenightandthedaytheywouldbothlaughatyouthemountainveiledinmistisnotahillanoaktreeintherainisnotaweepingwillowbeholdhereisaparadoxthedeepandhigharenearertooneanotherthanthemidleveltoeitherwhenistoodaclearmirrorbeforeyouyougazedintomeandsawyourimagethenyousaidiloveyoubutintruthyoulovedyourselfinmewhenyouenjoylovingyourneighboritceasestobeavirtuelovewhichisnotalwaysspringingisalwaysdyingyoucannothaveyouthandtheknowledgeofitatthesametimeforyouthistoobusylivingtoknowandknowledgeistoobusyseekingitselftoliveyoumaysitatyourwindowwatchingthepassersbyandwatchingyoumayseeanunwalkingtowardyourrighthandandaprostitutetowardyourlefthandandyoumaysayinyourinnocencehownobleistheoneandhowignobleistheotherbutshouldyoucloseyoureyesandlistenawhileyouwouldhearavoicewhisperingintheetheroneseeksmeinprayerandtheotherinpainandinthespiritofeachthereisabowerformyspiritonceeveryhundredyearsjesusofnazarethmeetsjesusofthechristianinagardenamongthehillsoflebanonandtheytalklongandeachtimejesusofnazarethgoesawaysayingtojesusofthechristianmyfriendifearweshallneverneveragreemaygodfeedtheoverabundantagreatmanhastwoheartsonebleedsandtheotherforbearsshouldonetellaliewhichdoesnothurtyounoranyoneelsewhynotsayinyourheartthatthehouseofhisfactsistoosmallforhisfanciesandhehadtoleaveitforlargerspacebehindeverycloseddoorisamysterysealedwithsevensealswaitingisthehoofsoftimewhatiftroubleshouldbeanewwindowintheeasternwallofyourhouseyoumayforgettheonewithwhomyouhavelaughedbutnevertheonewithwhomyouhavewepttheremustbesomethingstrangelysacredinsaltitisinourtearsandintheseaourgodinhisgraciousthirstwilldrinkusallthedewdropandthetearyouarebutafragmentofyourgiantselfamouththatseeksbreadandablindhandthatholdsthecupforathirstymouthifyouwouldrisebutacubitaboveraceandcountryandselfyouwouldindeedbecomegodlikeifiwereyouiwouldnotfindfaultwiththeseaatlowtideitisagoodshipandourcaptainisableitisonlyyourstomachthatisindisordershouldyousituponacloudyouwouldnotseetheboundarylinebetweenonecountryandanothernortheboundarystonebetweenafarmandafarmitisapityyoucannotsituponacloudsevencenturiesagosevenwhitedovesrosefromadeepvalleyflyingtothesnowwhitesummitofthemountainoneofthesevenmenwhowatchedtheflightsaidiseeablackspotonthewingoftheseventhdovetodaythepeopleinthatvalleytellofsevenblackdoveswhoflewtothesummitofthesnowymountainintheautumnigatheredallmysorrowsandburiedtheminmygardenandwhenaprilreturnedandspringcametowedtheearththeregrewinmygardenbeautifulflowersunlikeallotherflowersandmyneighborscametobeholdthemandtheyallsaidtomewhenautumncomesagainatseedingtimewillyounotgiveusoftheseedsoftheseflowersthatwemayhavetheminourgardensitisindeedmiseryifistretchanemptyhandtomenandreceivenothingbutitishopelessnessifistretchafullhandandfindnonetoreceiveilongforeternitybecausethereishallmeetmyunwrittenpoemsandmyunpaintedpicturesartisastepfromnaturetowardtheinfiniteaworkofartisamistcarvedintoanimageeventhehandsthatmakecrownsofthornsarebetterthanidlehandsourmostsacredtearsneverseekoureyeseverymanisthedescendantofeverykingandeveryslavethateverlivedifthegreatgrandfatherofjesushadknownwhatwashiddenwithinhimwouldhenothavestoodinaweofhimselfwastheloveofjudasmotherofhersonlessthantheloveofmaryforjesustherearethreemiraclesofourbrotherjesusnotyetrecordedinthebookthefirstthathewasamanlikeyouandmethesecondthathehadasenseofhumourandthethirdthatheknewhewasaconquerorthoughconqueredcrucifiedoneyouarecrucifieduponmyheartandthenailsthatpierceyourhandspiercethewallsofmyheartandtomorrowwhenastrangerpassesbythisgolgothahewillnotknowthattwobledherehewilldeemitthebloodofonemanyoumayhaveheardoftheblessedmountainitisthehighestmountaininourworldshouldyoureachthesummityouwouldhaveonlyonedesireandthattodescendandbewiththosewhodwellinthedeepestvalleythatiswhyitiscalledtheblessedmountaineverythoughtihaveimprisonedinexpressionimustfreebymydeedsflagishelloxnucagoodluck
#看结尾
#flag{helloxnucagoodluck}